Research
Onchain enforcement: A deep dive into stablecoin blacklisting
Blacklisting has become an essential part of stablecoin infrastructure. With over $1 billion in frozen assets, is onchain enforcement keeping pace?

Andres M, Range
·
Dec 9, 2025
As of late 2025, more than $1 billion in stablecoin assets have been frozen onchain by issuers across Ethereum, Solana, Tron, and other major networks. From sanctions enforcement to exploit mitigation, blacklisting has become an essential - but poorly understood - tool in the stablecoin issuer toolkit.
This third entry in our Stablecoin Onchain series presents the most detailed analysis yet of how blacklisting is used, where it's applied, and what that tells us about the evolution of stablecoin enforcement policy. The data shows a system that is proactive rather than reactive, highly discretionary, and overwhelmingly targeted at large actors - not broad compliance.
Be the first to read the next research piece by joining our mailing list >>
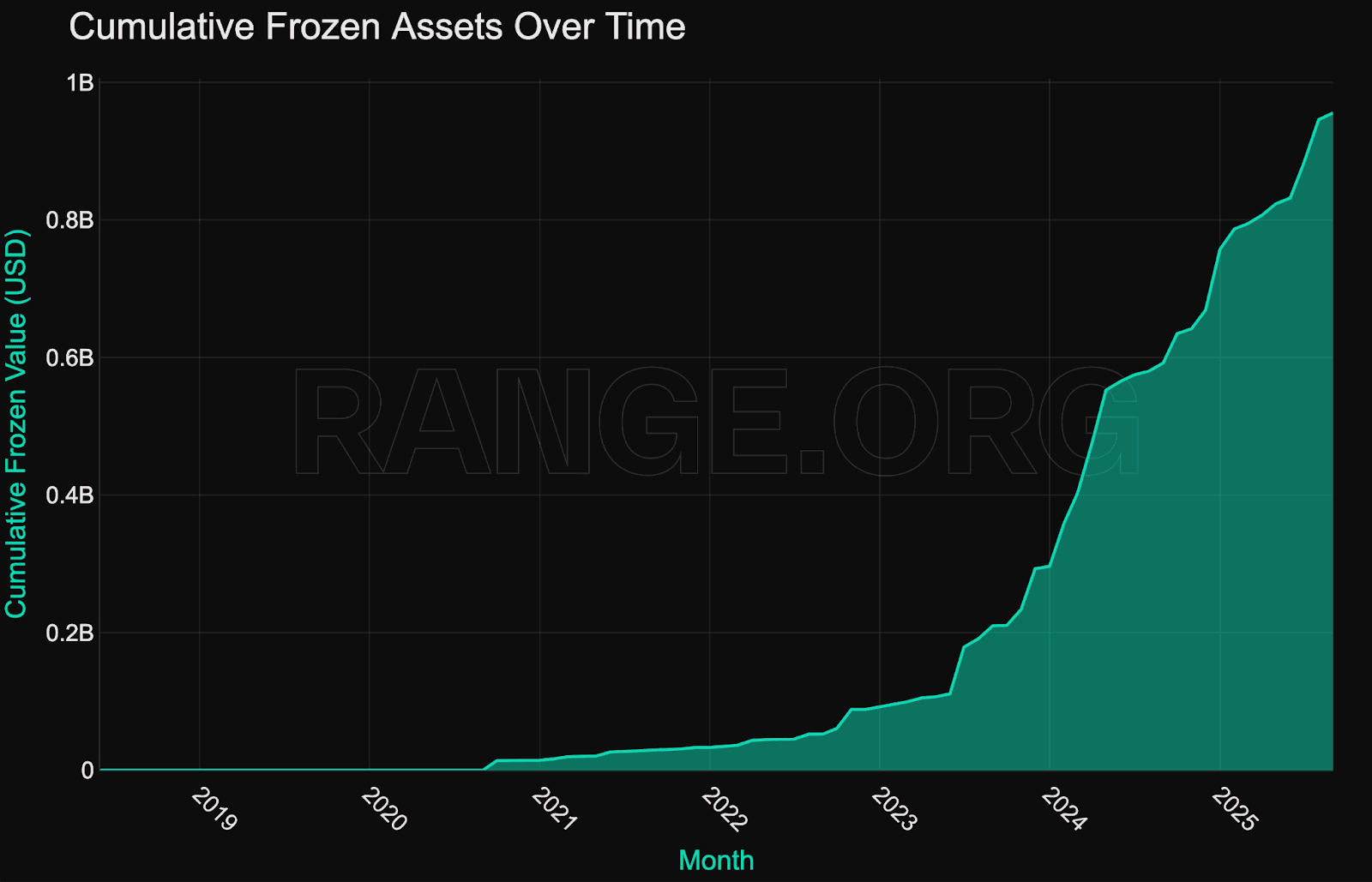
$1 billion frozen, so far
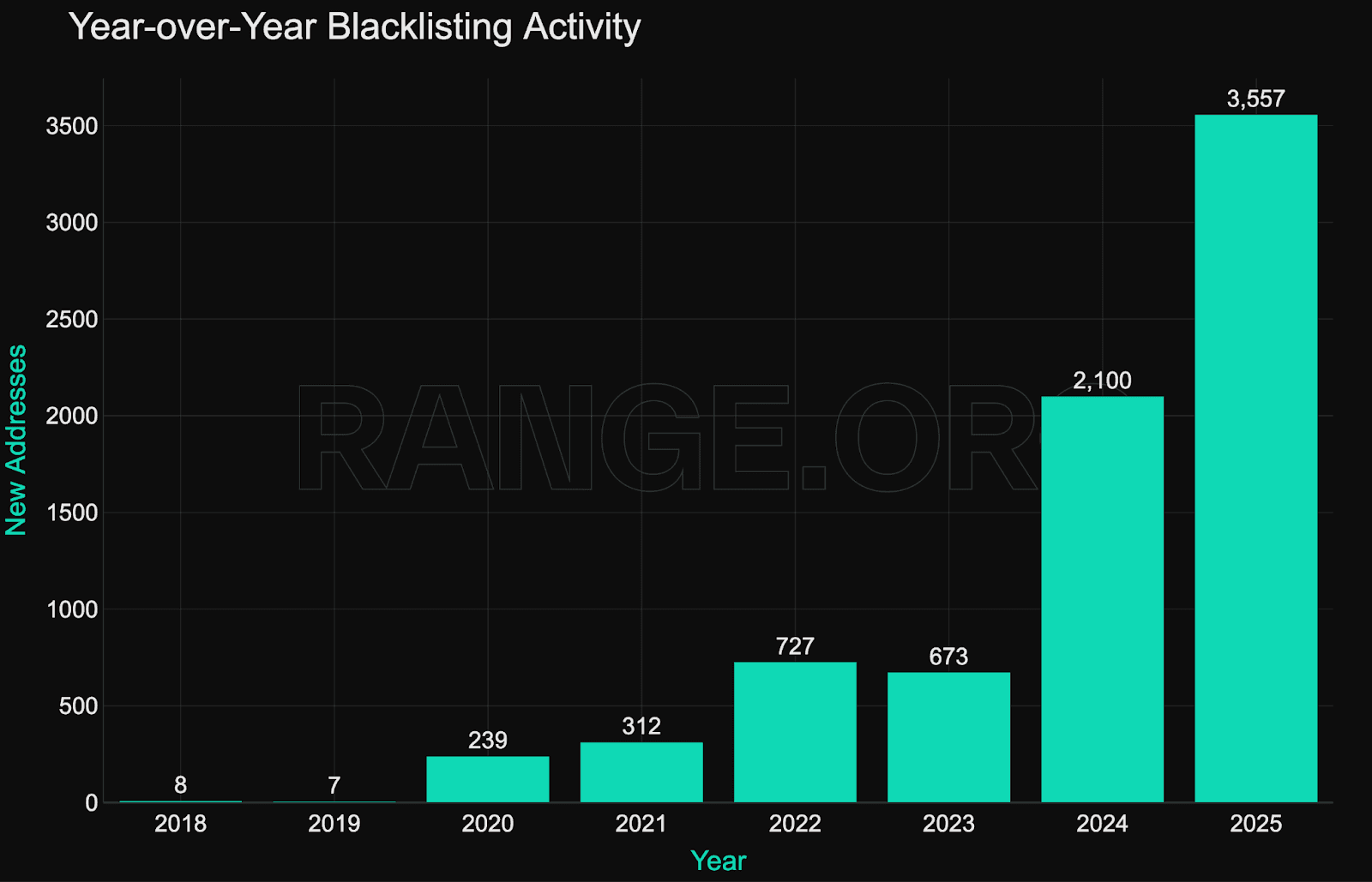
Blacklisting activity has expanded sharply over the past 24 months, becoming a key onchain enforcement mechanism for major stablecoin issuers. In 2025 alone, 4,320 new addresses were added to onchain deny-lists across Ethereum, Solana, Tron, and other networks - more than double the number from 2023.
Cumulative frozen value crossed the $1 billion mark this year, with enforcement velocity showing no signs of slowing.
This surge marks a shift in enforcement posture from occasional intervention to a regular operational function. Issuers are now likely operating active pipelines to screen, assess, and freeze addresses they deem high risk, as mandated by most regulators.
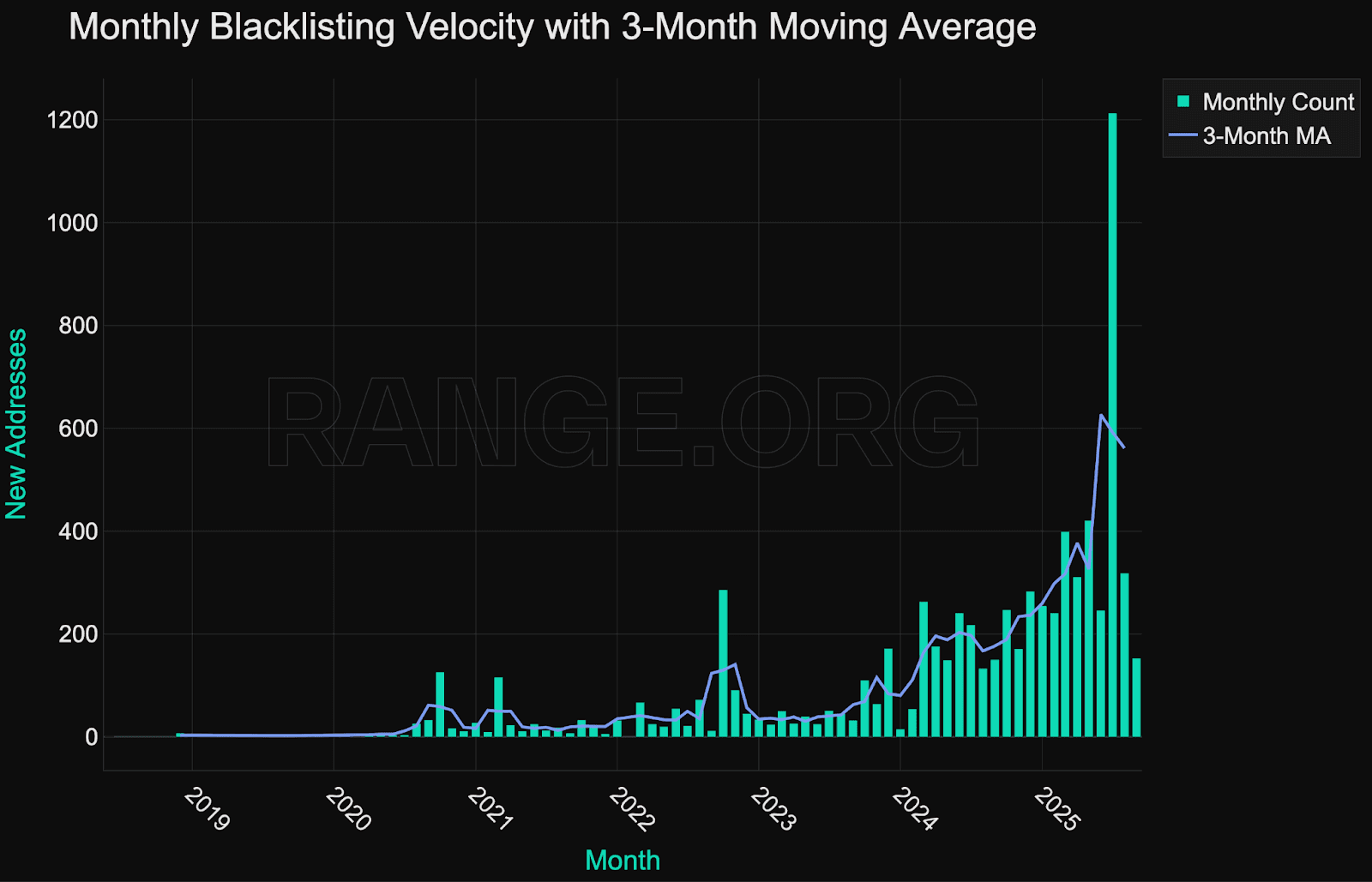
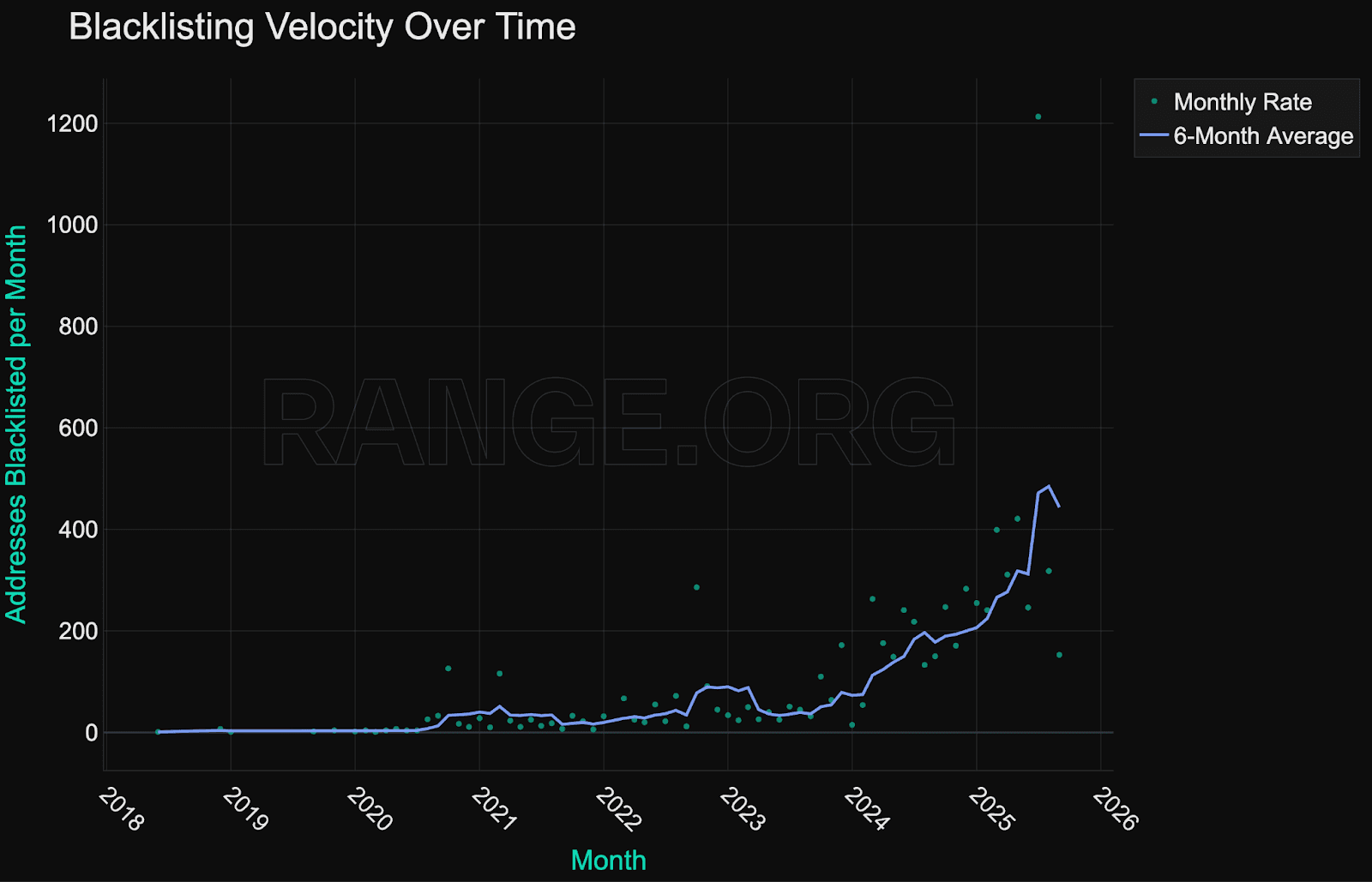
More mature, systematic enforcement
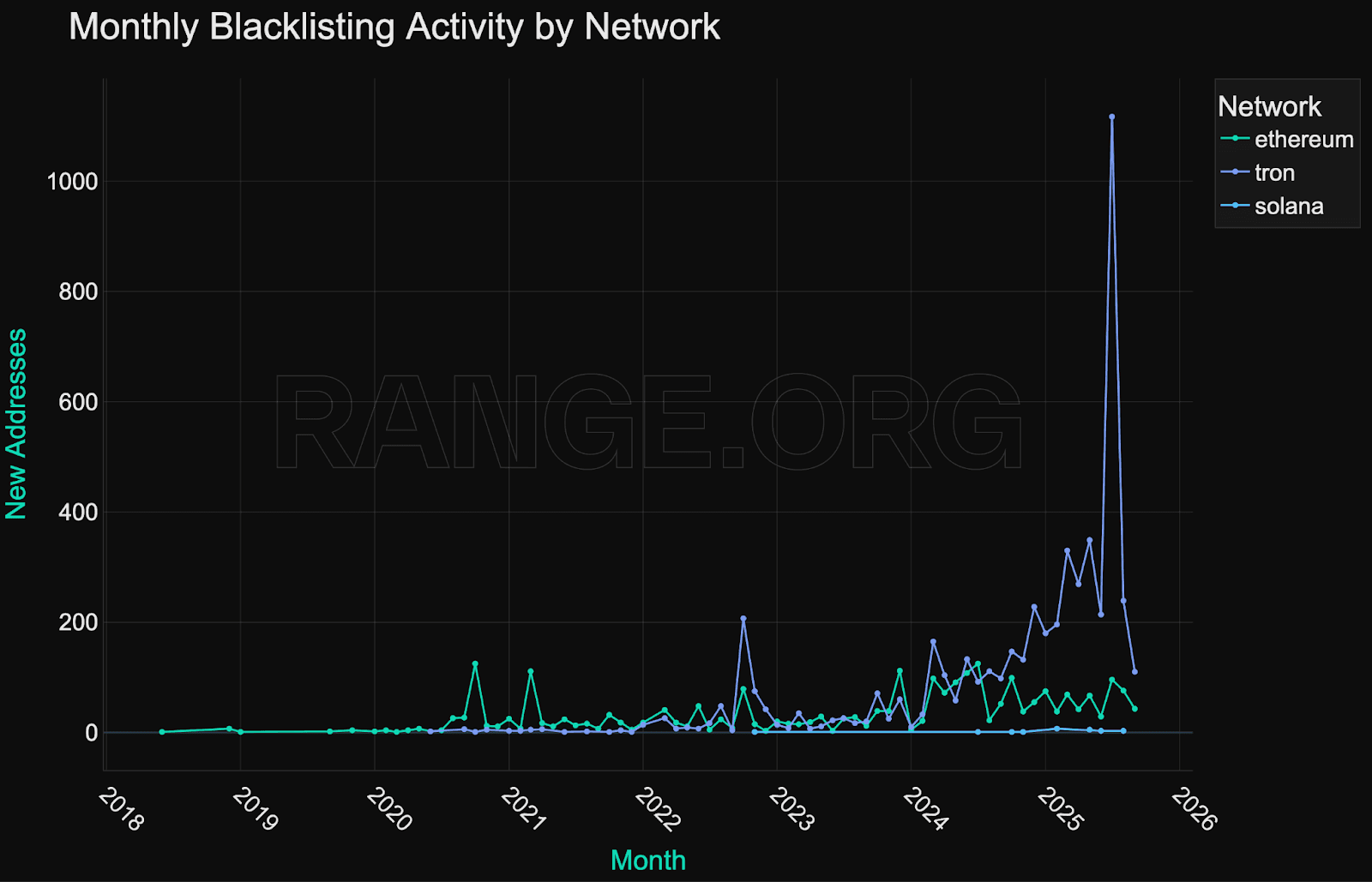
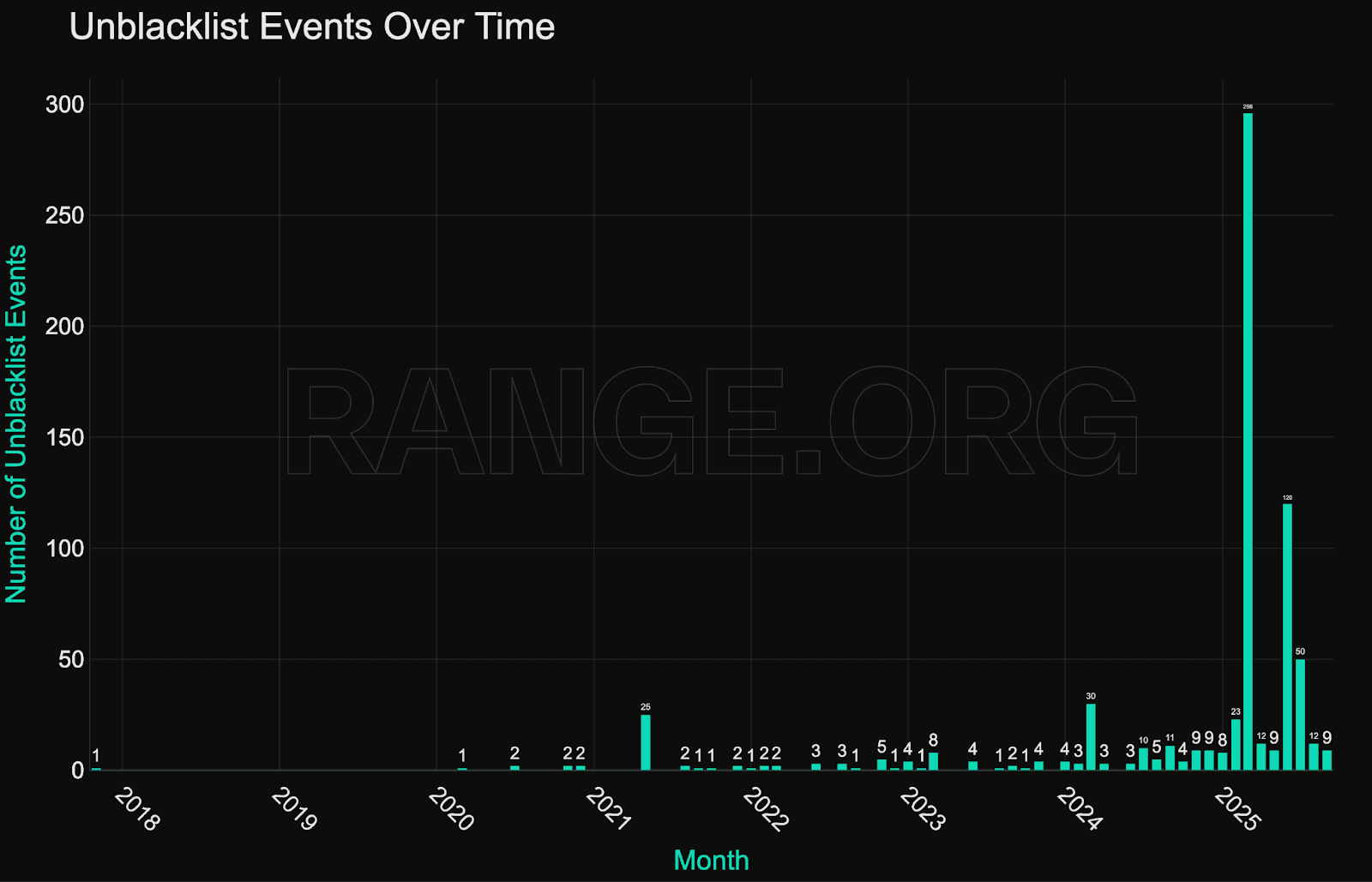
Monthly blacklisting activity peaked at over 1,200 addresses in mid-2025, mainly driven by large-scale batch enforcement on Tron. Unlike earlier years, where blacklisting events were typically linked to isolated hacks or external enforcement triggers, 2025 reflects sustained, recurring enforcement across multiple networks.
This pattern suggests adopting more mature, systematic enforcement pipelines, likely supported by internal analytics or external monitoring integrations such as Range.
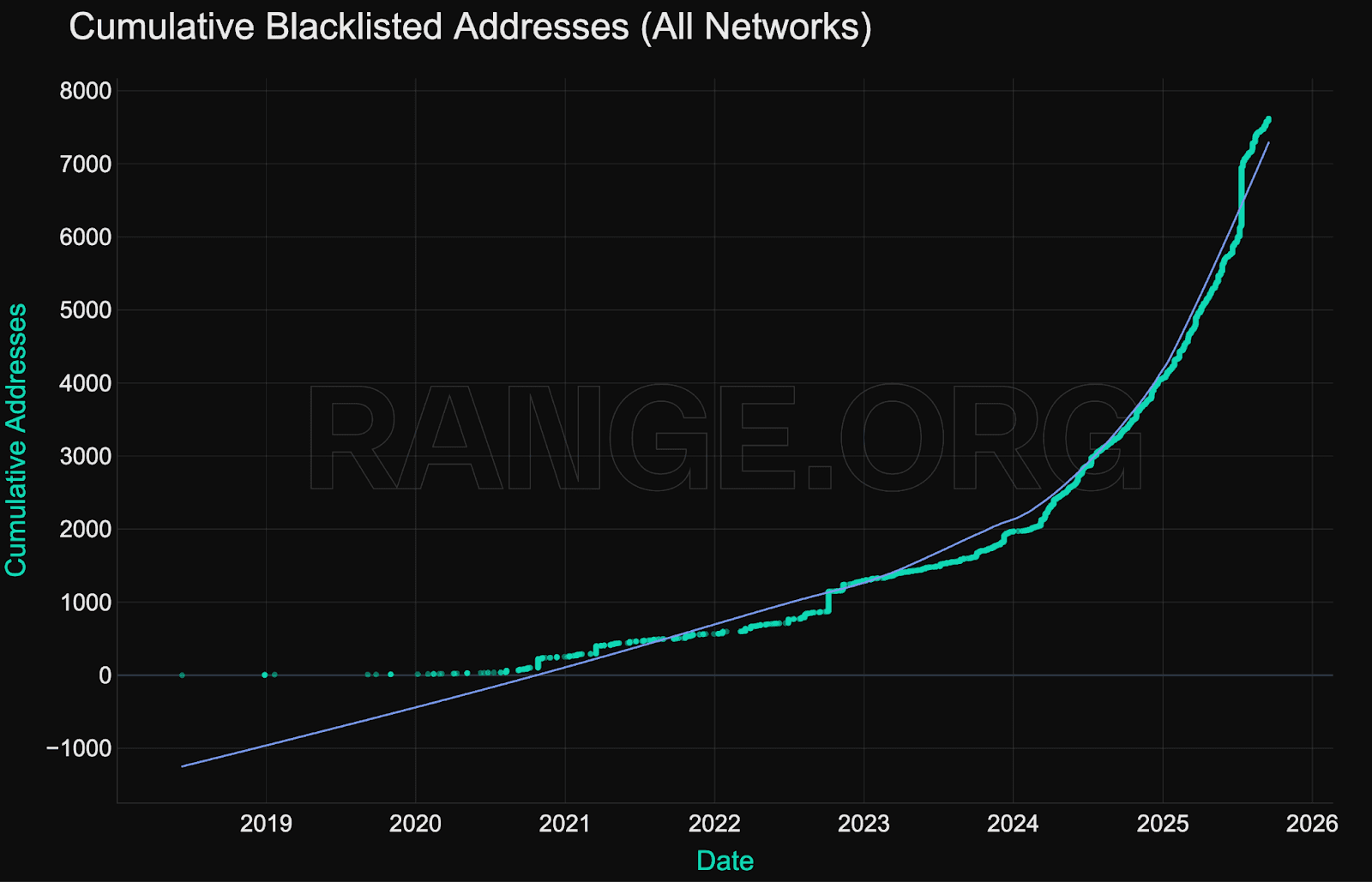
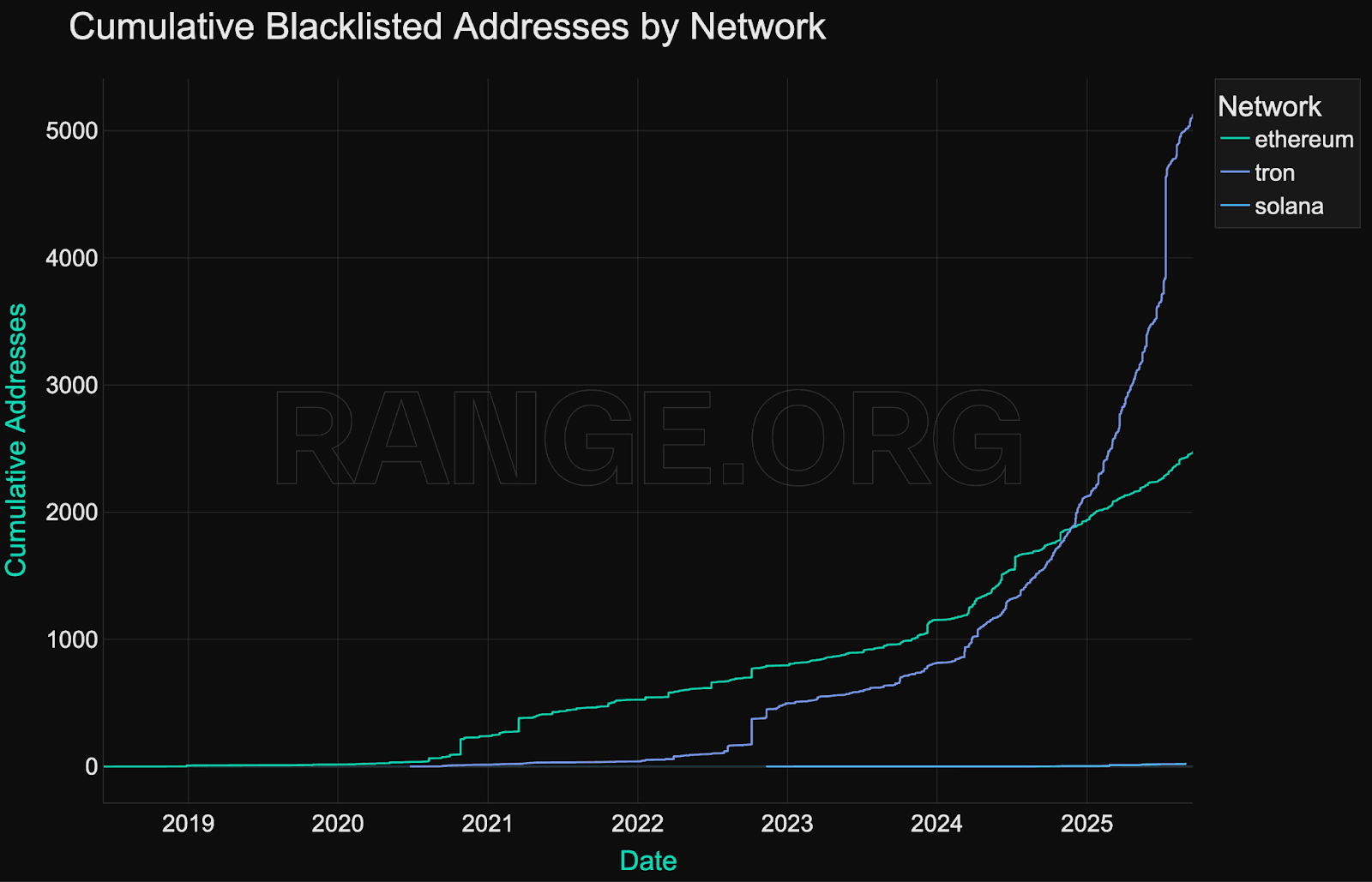
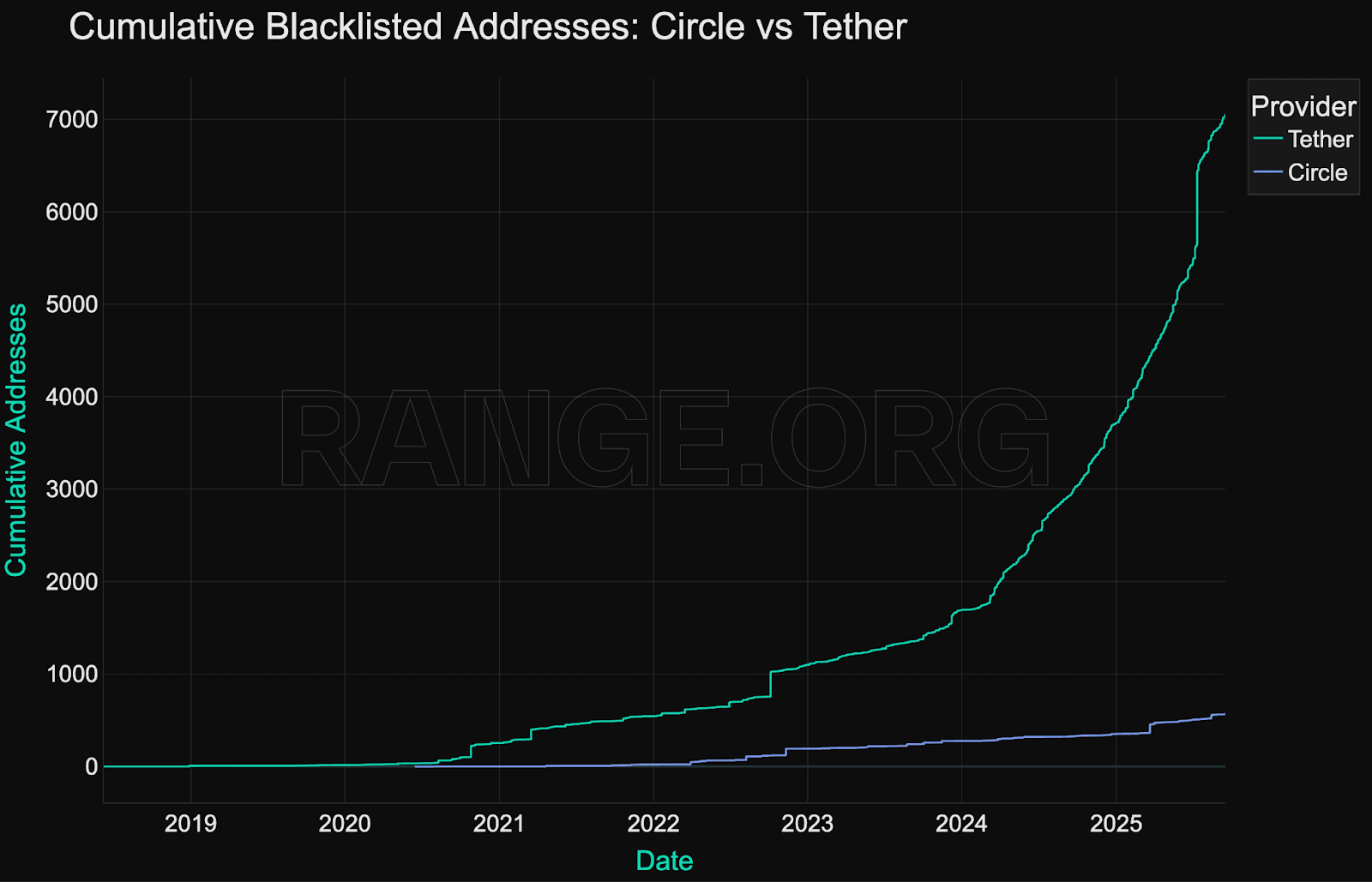
Cumulative growth in blacklisted addresses
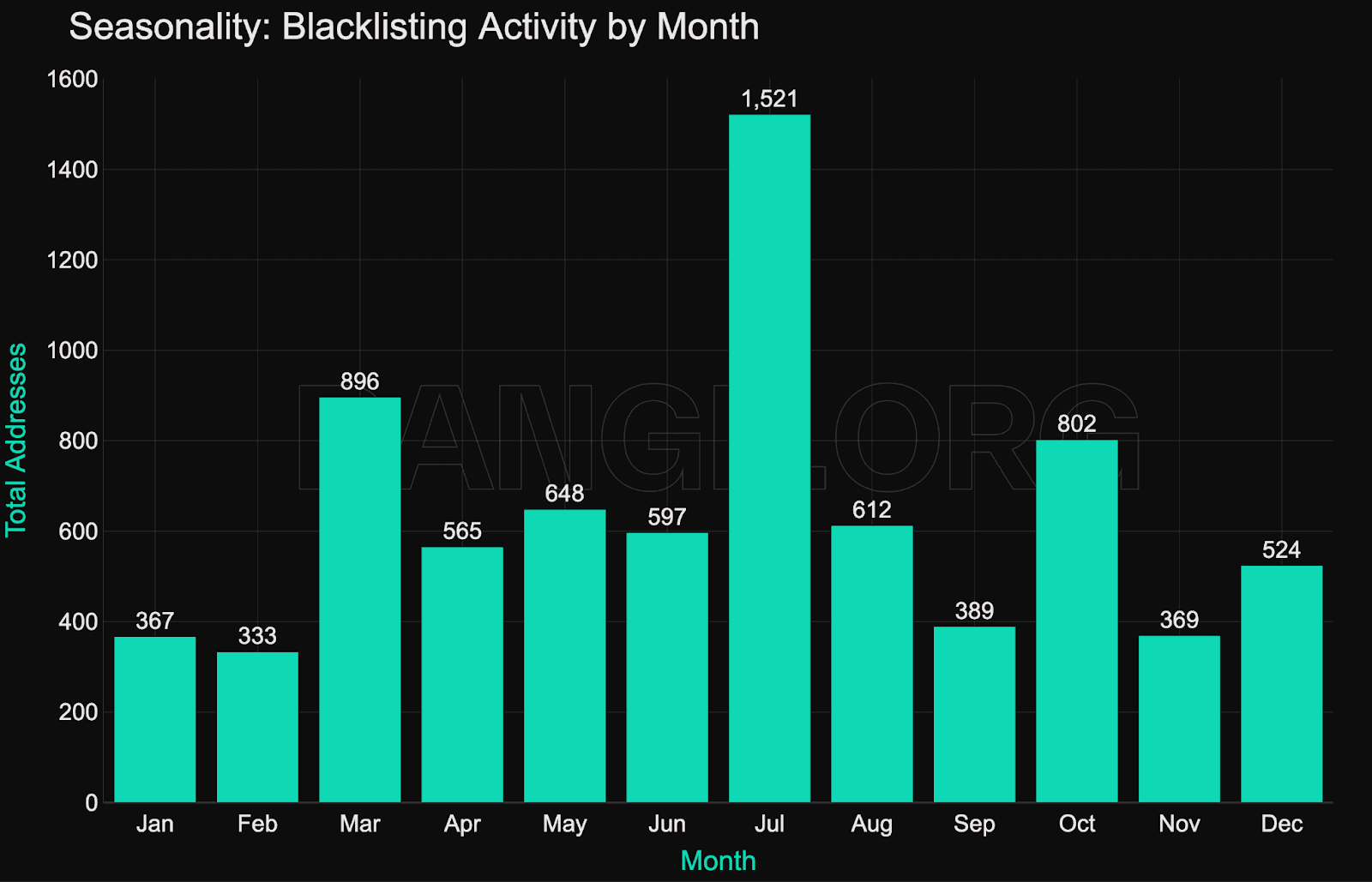
As of Q4 2025, more than 8,000 unique addresses have been blacklisted onchain by stablecoin issuers. This includes both high-value incidents and broader activity targeting lower-balance wallets (e.g., phishing rings, spam contracts, or botnets).
While there are month-to-month deviations, with spikes in blacklisting activity sometimes driven by major hacks and exploits, there are no visible seasonality patterns in blacklisting activity.
The growth in blacklisting activity is effectively nonlinear, reflecting both decreased risk appetite and improving internal tooling within issuer compliance teams.
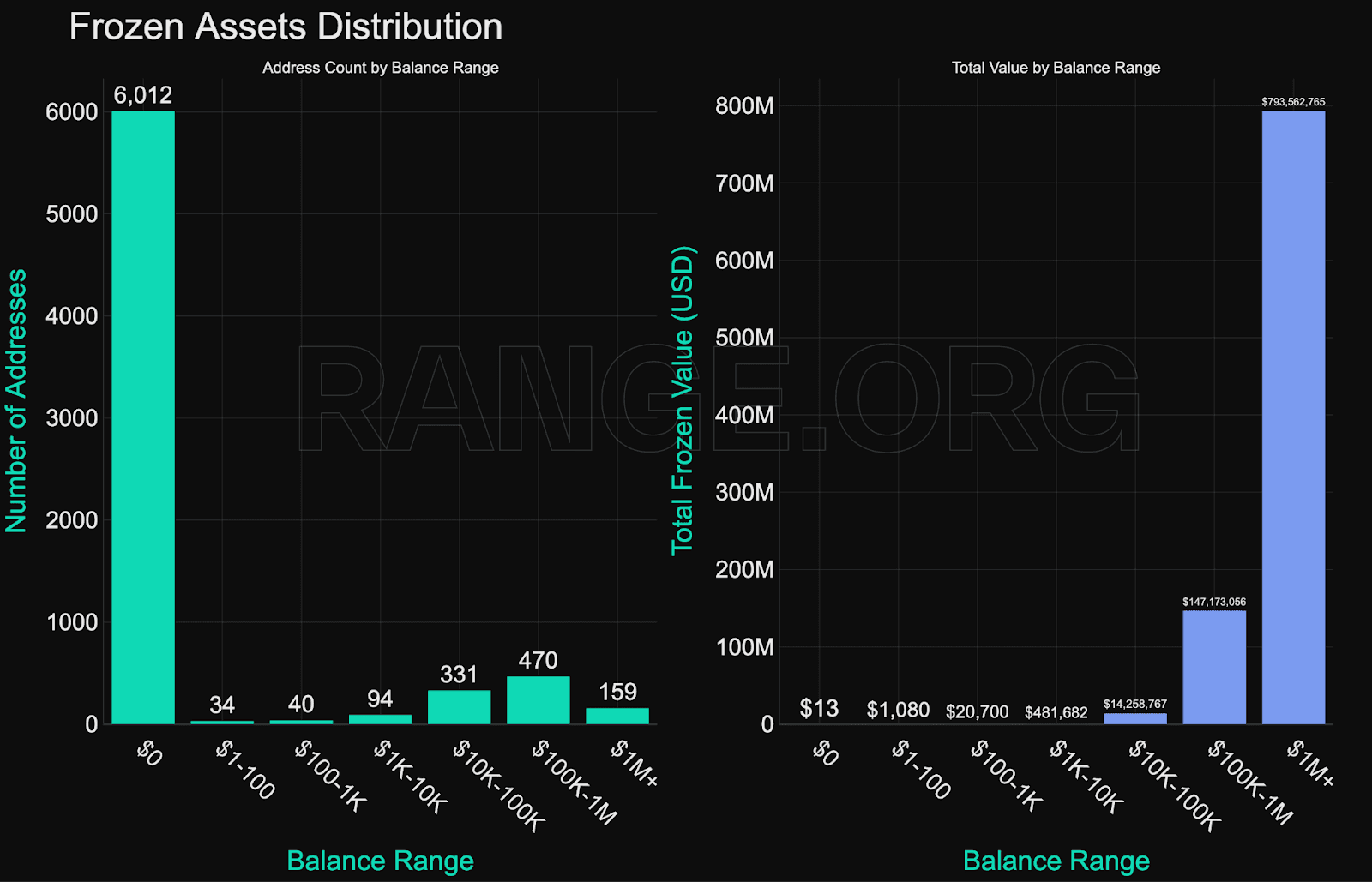
Zero-Balance Freezes
Despite the growing number of blacklisted addresses, most enforcement actions fail to capture active funds. Over 6,000 of the blacklisted addresses had a zero balance at the time of enforcement.
This strange activity highlights a critical timing issue:
In many cases, enforcement trails the actual movement of funds.
Attackers or flagged users often exit positions before issuer action is executed onchain.
Specifically in the case of Tether, due to the multisig requirements of their operational wallets, there is a lag between the initiation of a freeze call and its actual execution. During this time, the address of the targeted account is viewable onchain, which could alert the wallet owner to move their funds.
These findings underscore the need for faster detection-to-enforcement loops, particularly in cases involving stolen funds or known exploit routes.
Unlike other providers that simply flag sanctioned or issuer-flagged addresses, Range’s Risk API provides near real-time wallet screening, actively flagging wallets linked to ongoing issues, even as the attacker moves funds across chains.
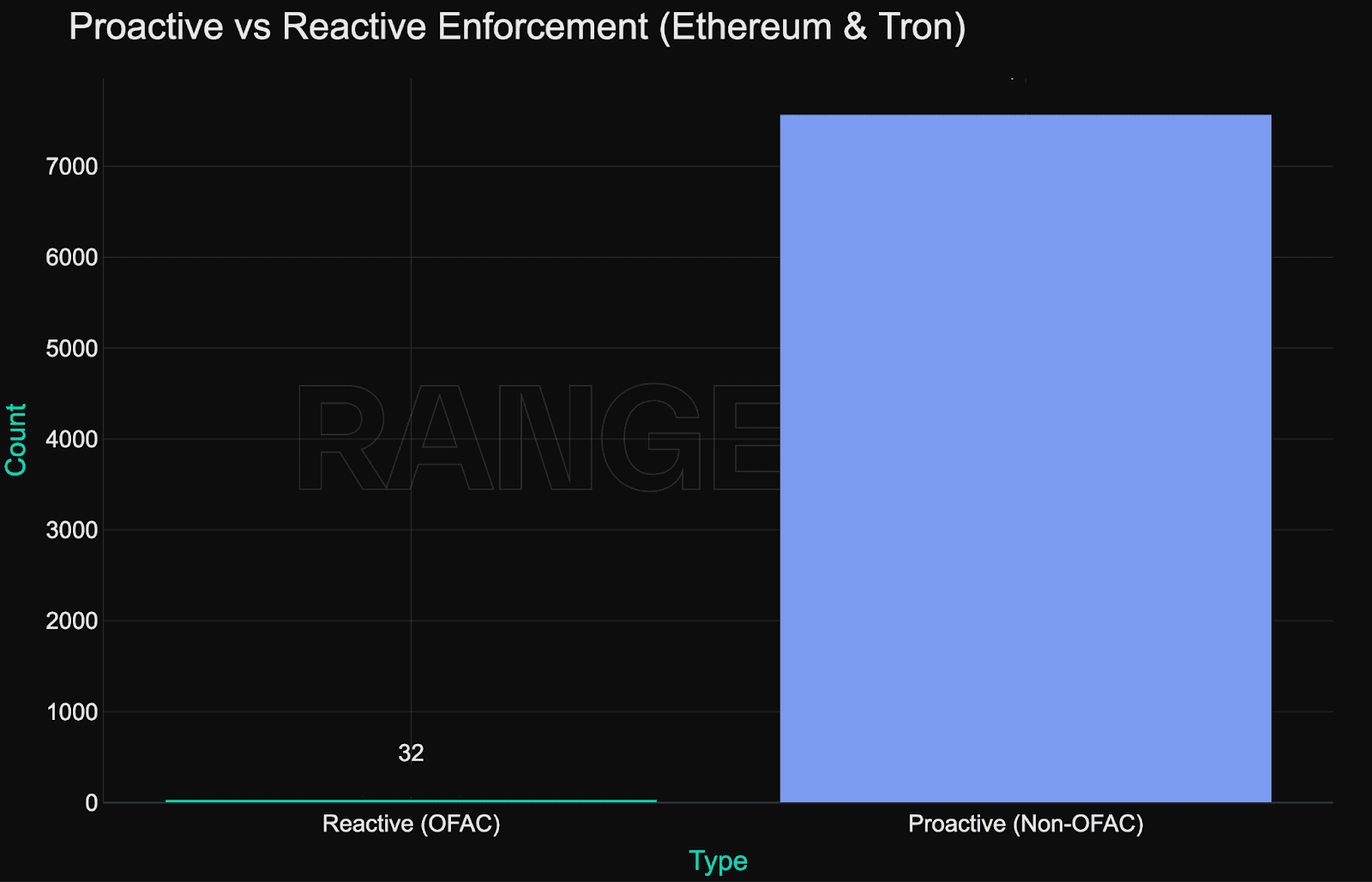
Enforcement is mainly proactive, not sanctions-based
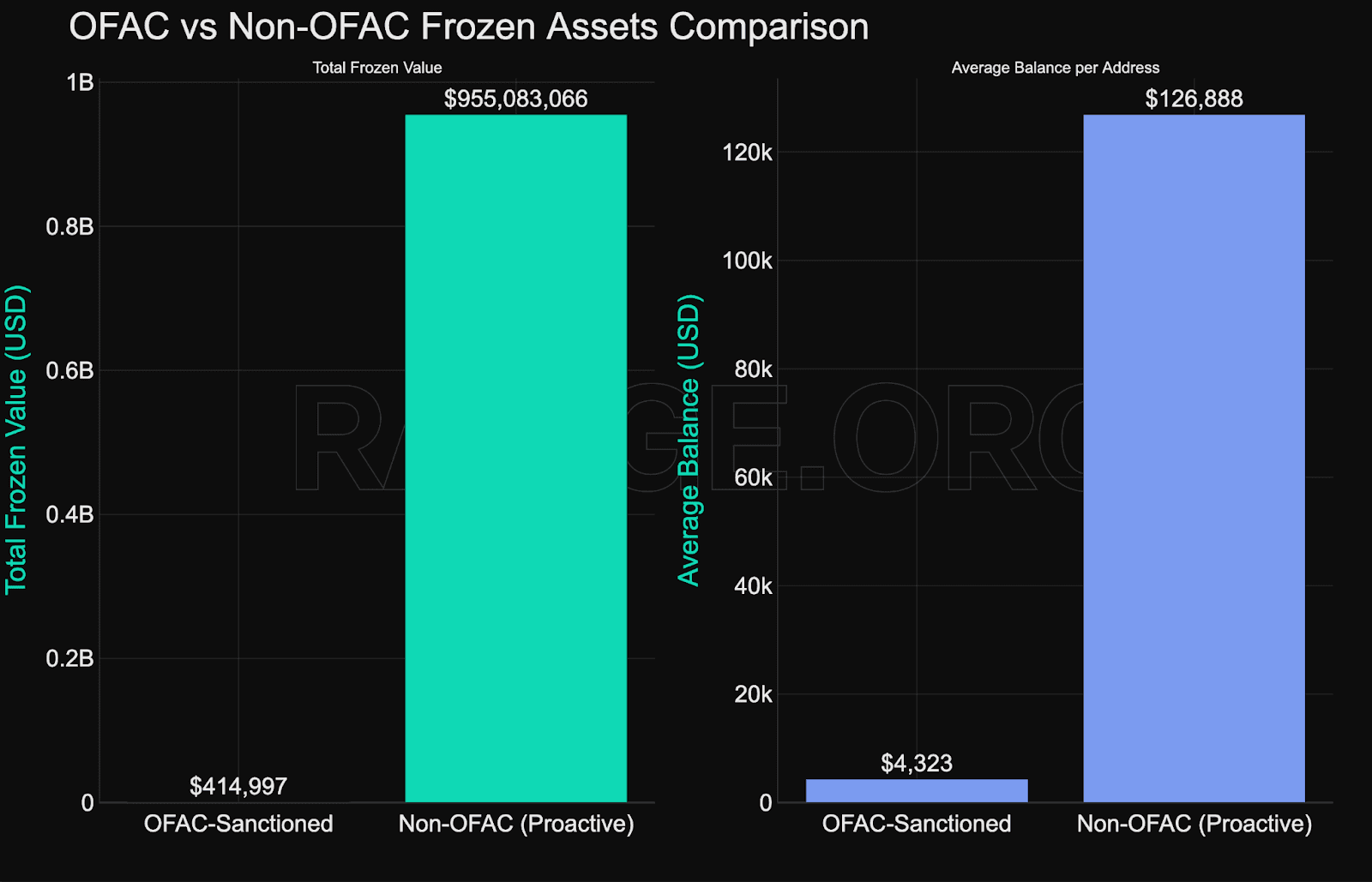
One of the clearest insights from the data: issuer-led enforcement dominates, while traditional sanctions compliance plays a minor role.
Only 0.04% of the total frozen value - $419,320 - is tied to OFAC-sanctioned addresses. Even among addresses that are on sanctions lists:
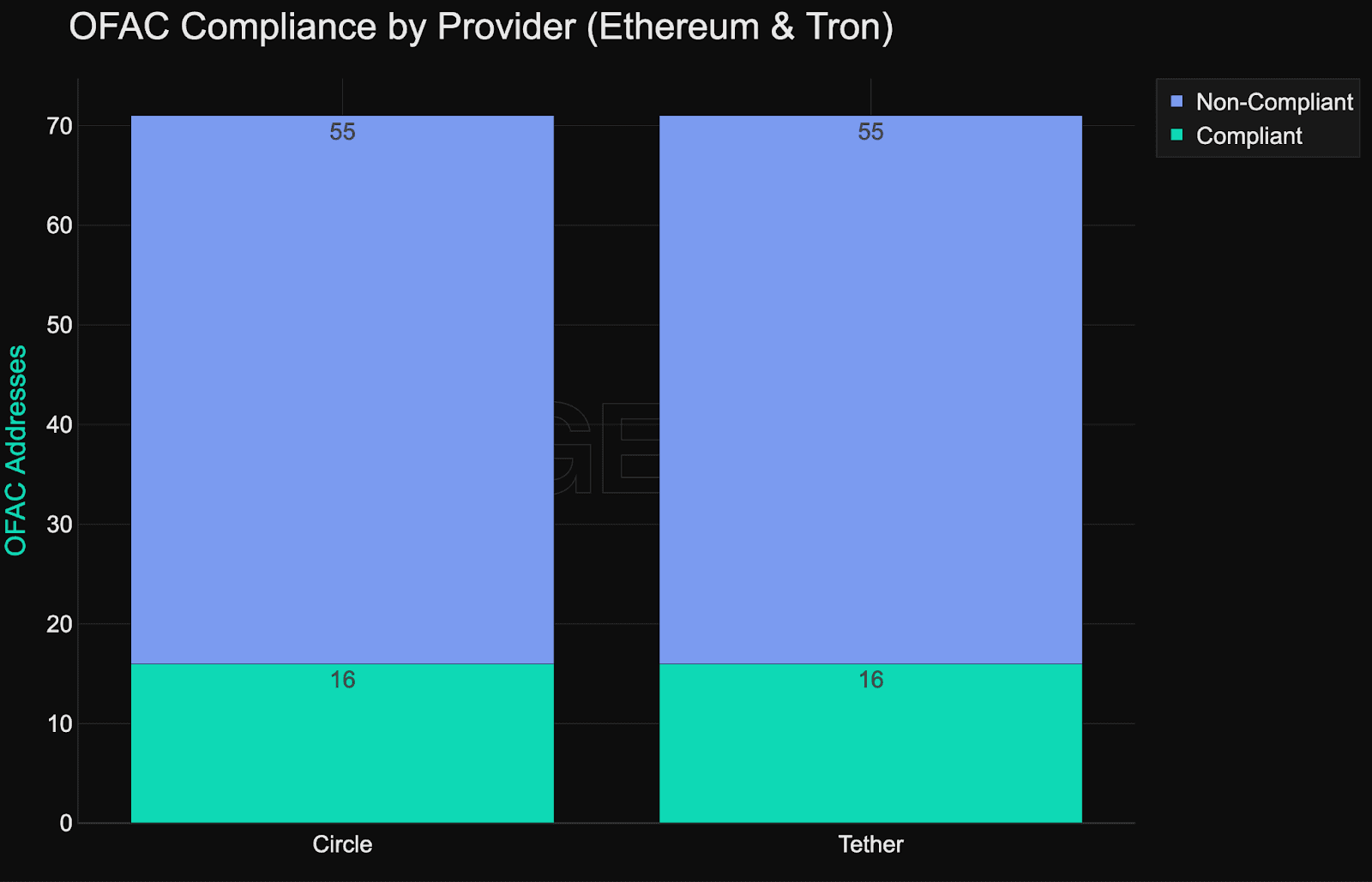
Only 36% of OFAC-listed stablecoin addresses are currently blacklisted.
Circle and Tether each missed at least 55 OFAC addresses.
In two notable cases, addresses were blacklisted before OFAC issued a designation.
This mismatch highlights a key point: blacklisting is not driven by regulatory lists alone. Instead, issuers appear to rely on internal risk detection, incident reports, or ecosystem feedback, resulting in a much broader, more discretionary enforcement scope. Incident reports usually come from teams like zeroShadow - who track the flow of illicit funds across chains, and coordinate with issuers and protocols to freeze them.
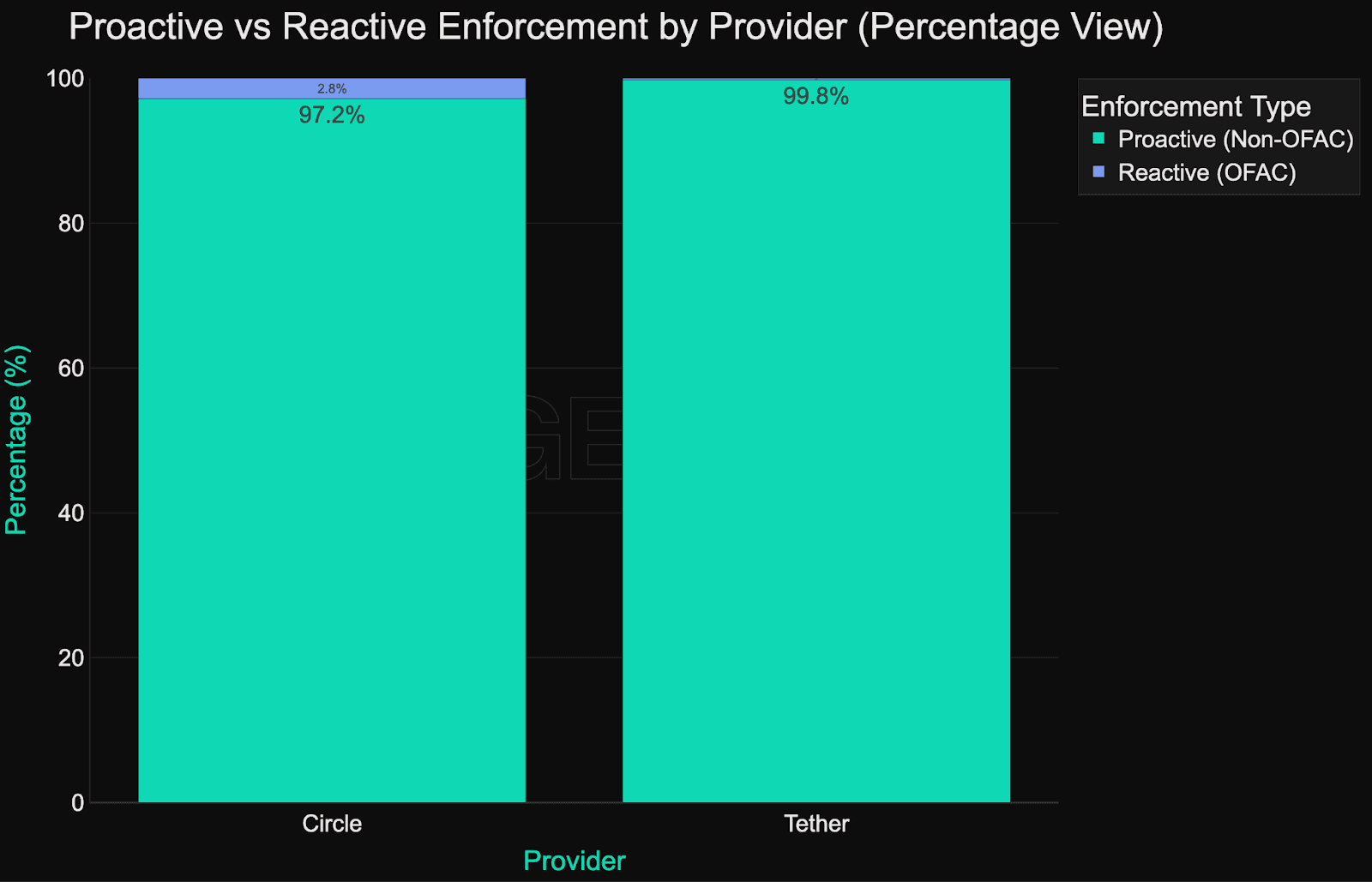
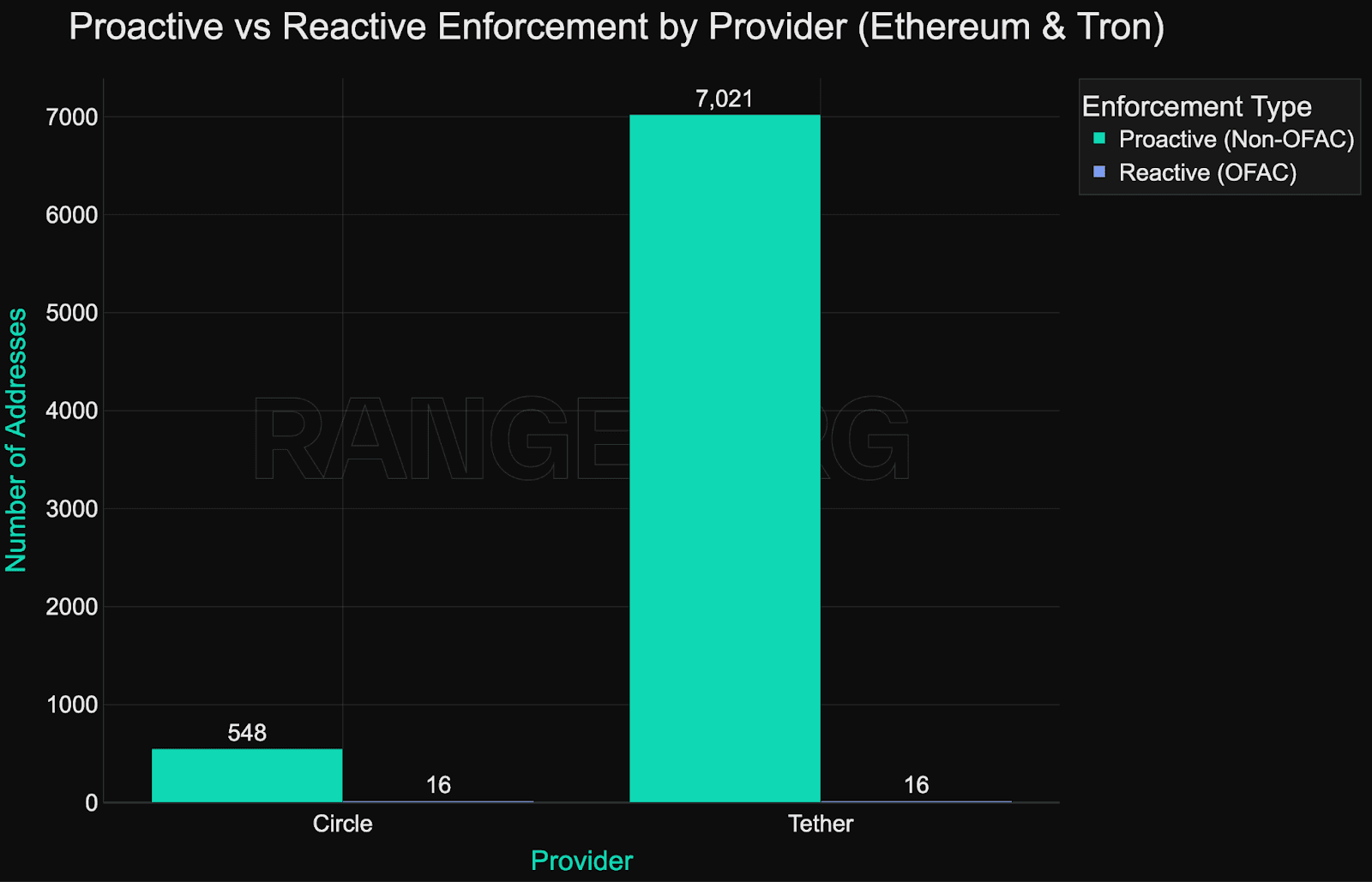
When comparing the two largest stablecoin issuers - Circle (USDC) and Tether (USDT), there is a clear difference in their level of proactivity:
Tether has proactively blocked 7,021 addresses on Ethereum and Tron
While Circle has proactively blocked just 548 addresses on those same networks
However, given Circle’s overall smaller blacklisting footprint, these 548 addresses represented 97.2% of addresses blacklisted by Circle, while Tether’s proactive blacklisting activity was 99.8% of its total blacklist.
It’s important to note that while Circle has unblacklisted some addresses, according to zeroShadow, they are generally resistant to blacklisting and reminting tokens. This reluctance has led to law enforcement agencies to generally avoid making requests for temporary freezes to Circle, since there is no benefit to the victim. This could explain the lower blacklisting activity on USDC (vs USDT).
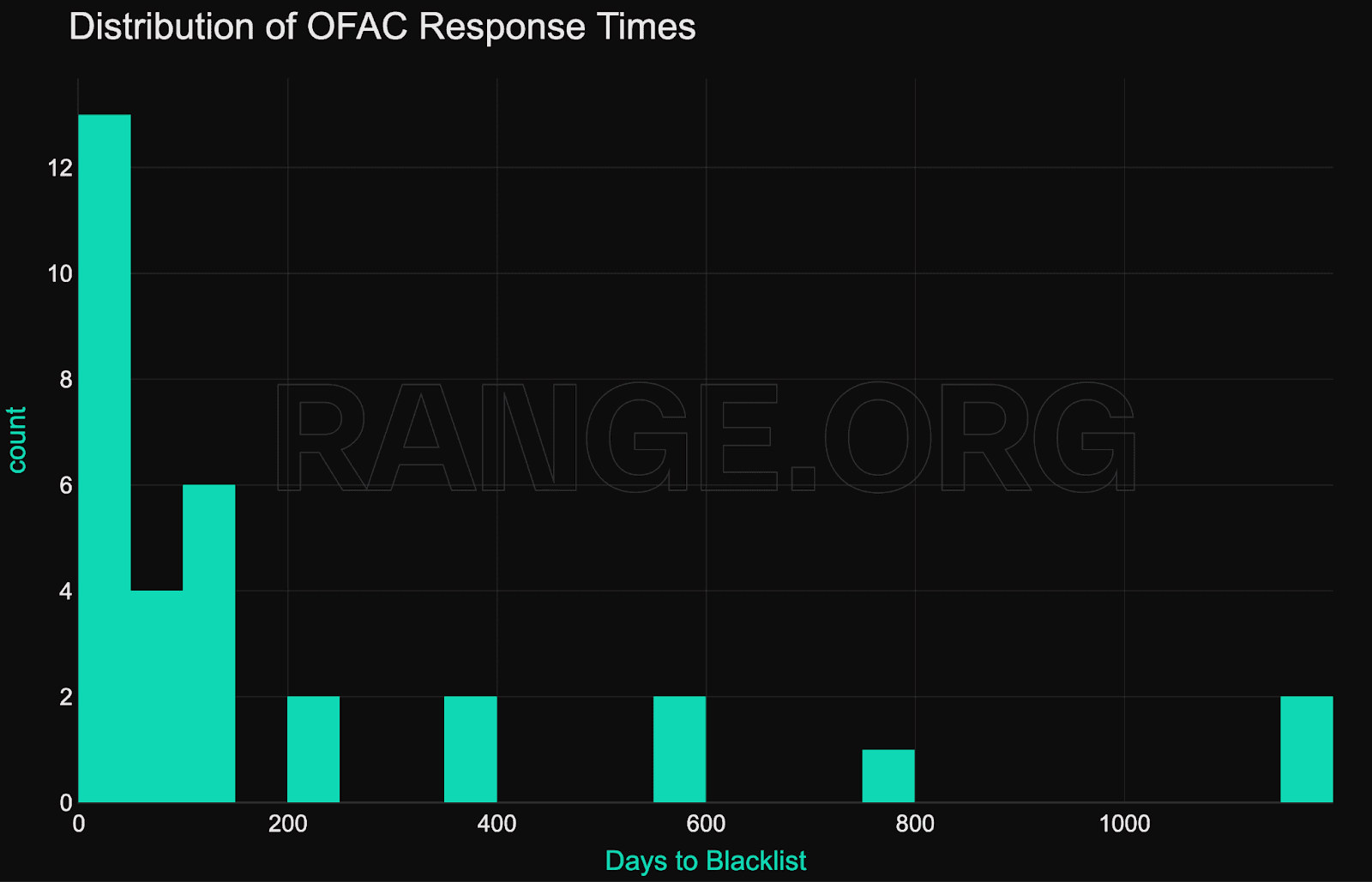
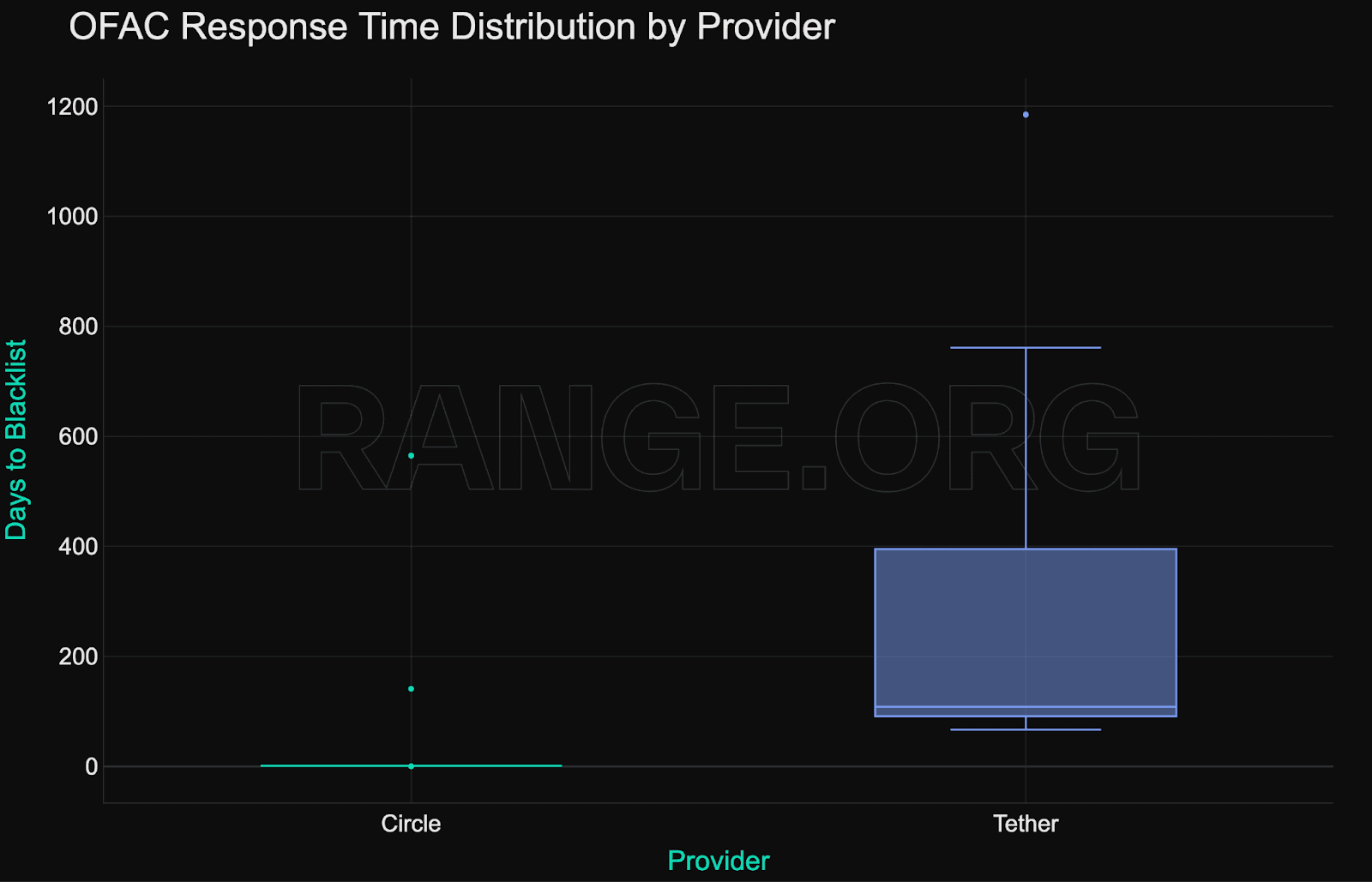
OFAC compliance among stablecoin issuers is inconsistent. Both Circle and Tether failed to blacklist at least 55 addresses that were officially sanctioned, while each only managed to enforce on 16 OFAC-listed addresses correctly. In total, just 36.4% (32 out of 88) of all OFAC-sanctioned stablecoin addresses have been blacklisted onchain.
Most sanctioned addresses are frozen relatively quickly - often within 24 hours, and typically within a week of being published by OFAC. However, a small number of addresses experience significant delays, with enforcement actions in some cases taking months or even years to occur. Circle is generally much faster at complying with OFAC sanctions than Tether.
Inconsistent enforcement of OFAC sanctions creates real challenges for DeFi protocols seeking to maintain compliance. Neither Circle nor Tether reliably covers sanctioned addresses - even for high-profile designations - and this analysis doesn’t even account for regional or jurisdiction-specific blocklists (e.g., EU, UK, or Singapore), which are increasingly relevant to teams operating or deploying globally.
Relying solely on issuer-level blacklisting from Circle or Tether is not sufficient for meeting regulatory obligations - especially for protocols with user-facing frontends or operational exposure in regulated jurisdictions.
Products like Range’s Faraday, which aggregate and normalize onchain enforcement data across multiple issuers and integrate external sanctions lists, can provide a more comprehensive and up-to-date foundation for DeFi compliance and risk screening.
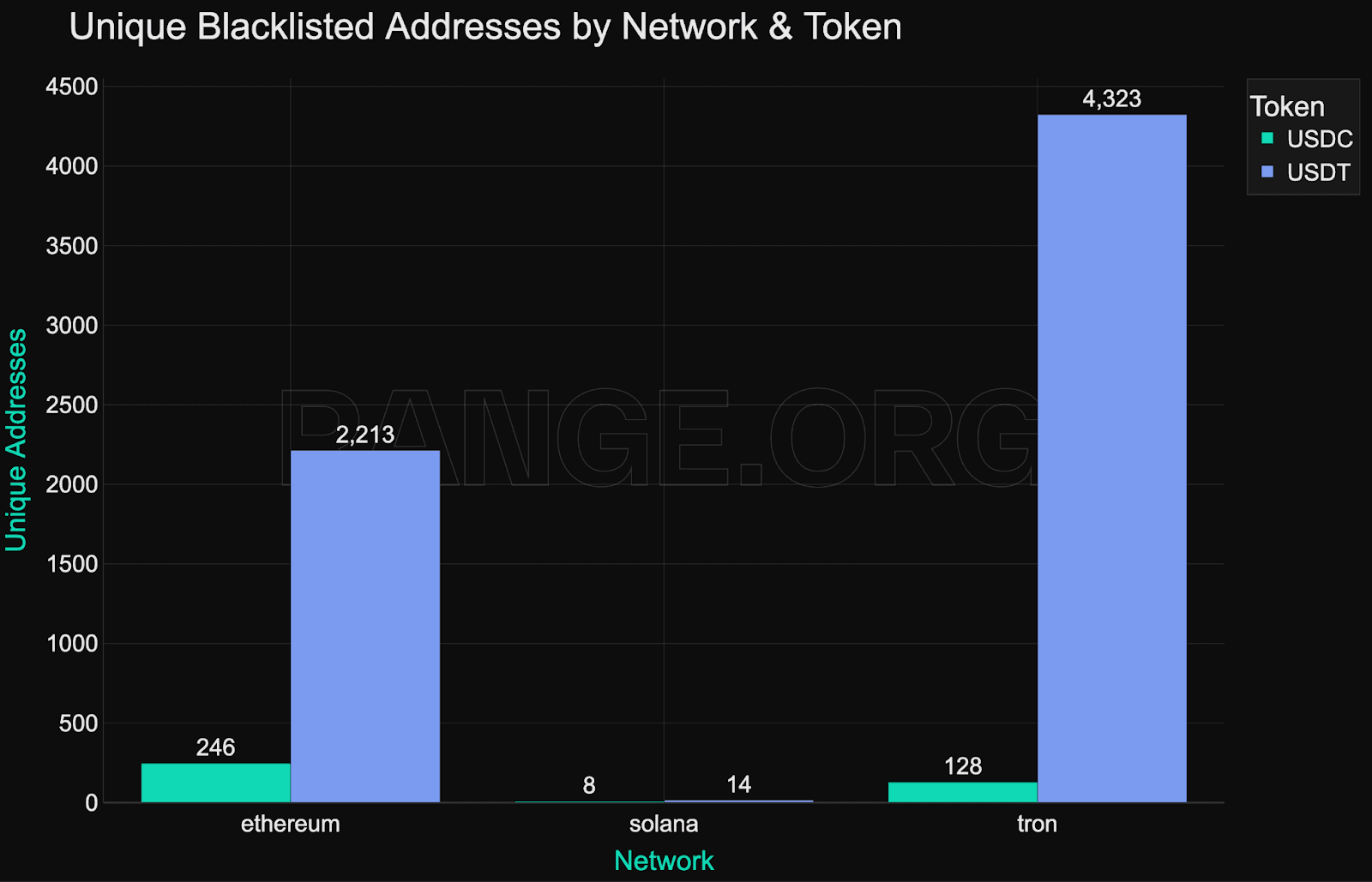
Blacklisting activity by network and provider
Blacklisting activity varies widely across networks - not just in volume, but in intent, structure, and provider dominance. While Ethereum leads in enforcement frequency and value, Tron dominates in batch size, and Solana shows the most discretion per event.
Ethereum
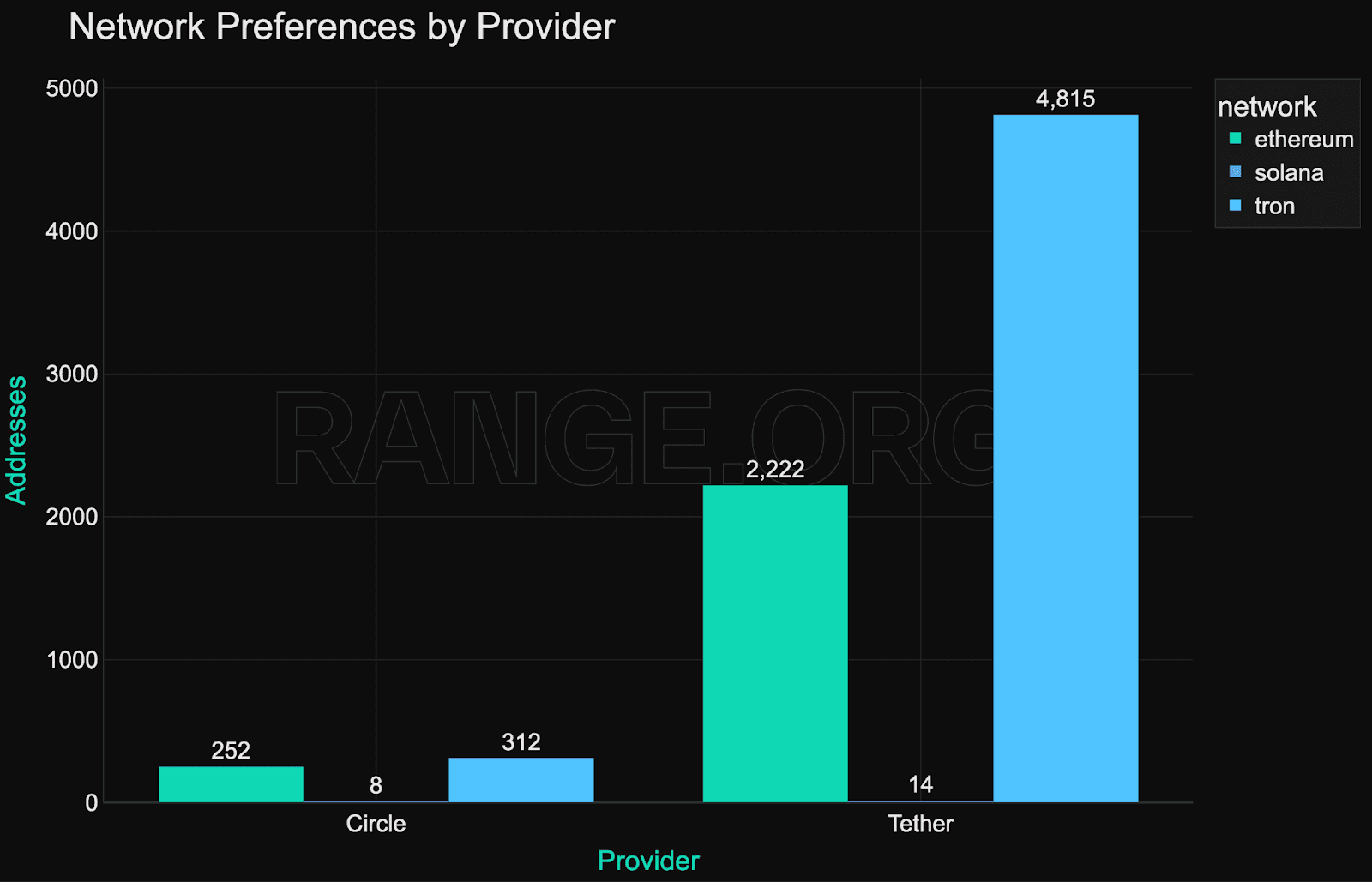
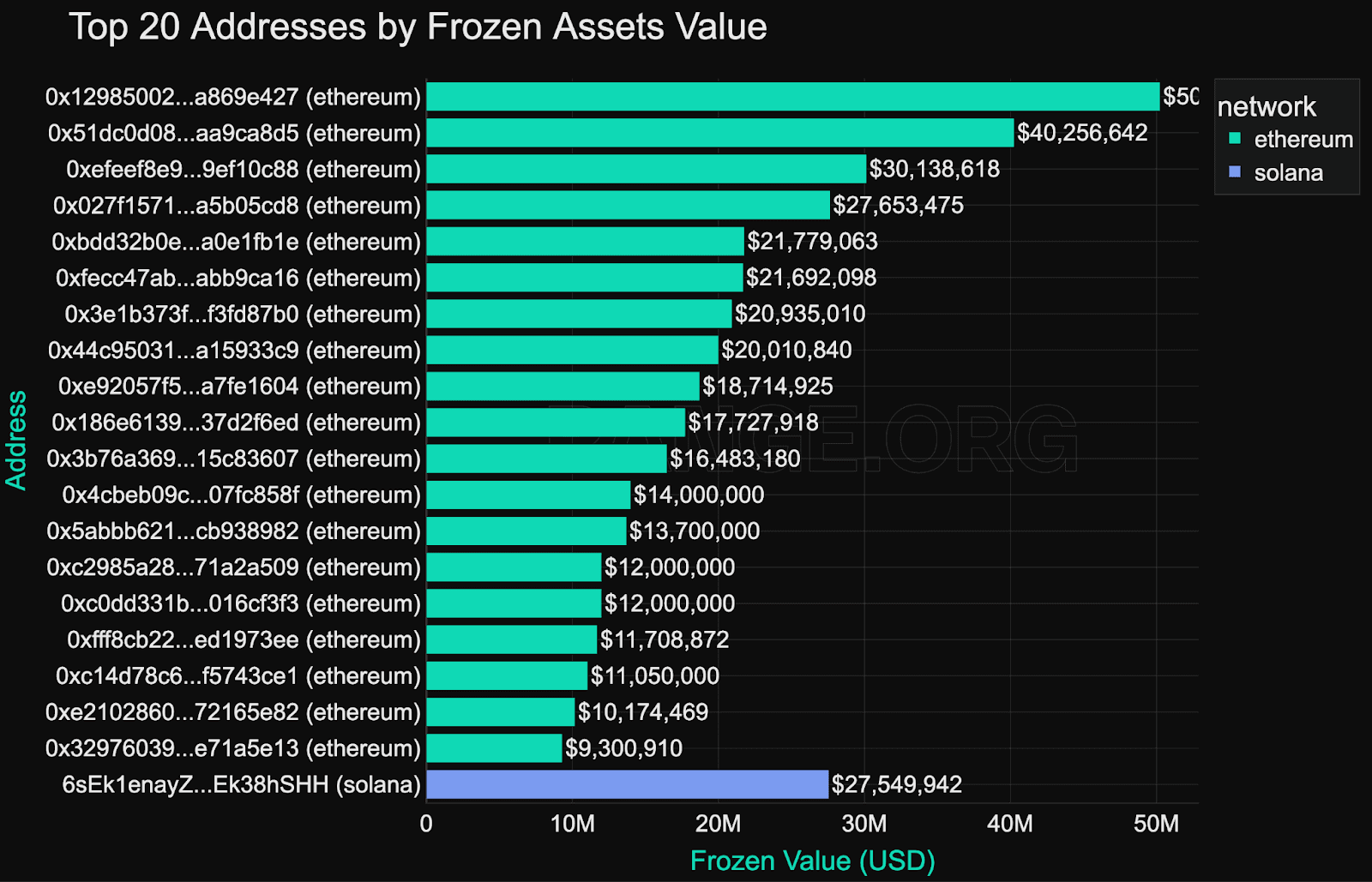
Ethereum is the most consistently enforced network, particularly by Circle, which has blacklisted over 2,700 addresses on Ethereum alone. It’s also where most high-value targets reside - all of the top 20 frozen wallets are on Ethereum, with balances ranging from $11 million to $50 million.
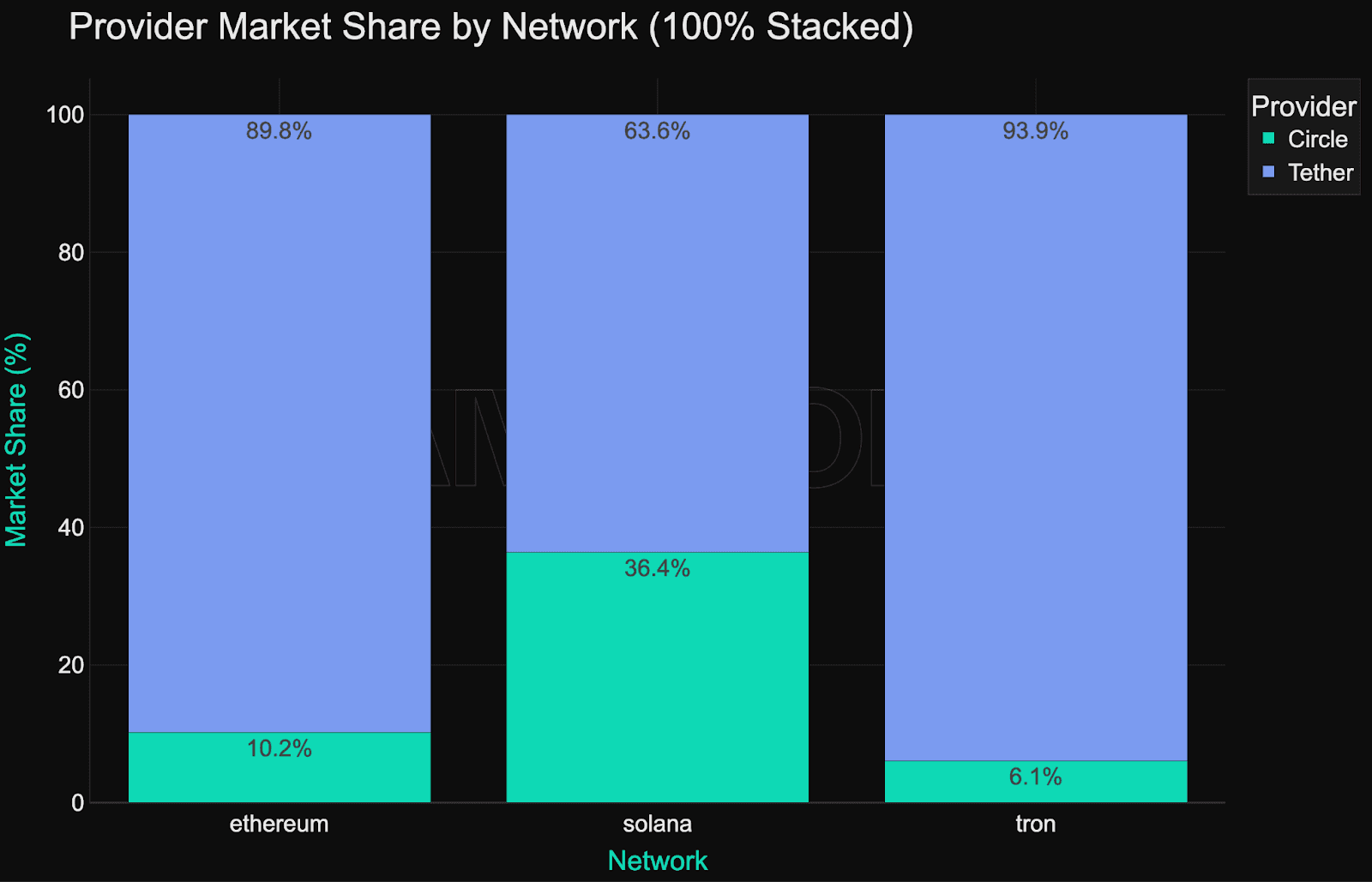
Circle maintains roughly 16% market share in Ethereum blacklisting activity, with the rest carried by Tether. This distribution suggests that enforcement on Ethereum is used for both systemic incidents and targeted high-value interventions.
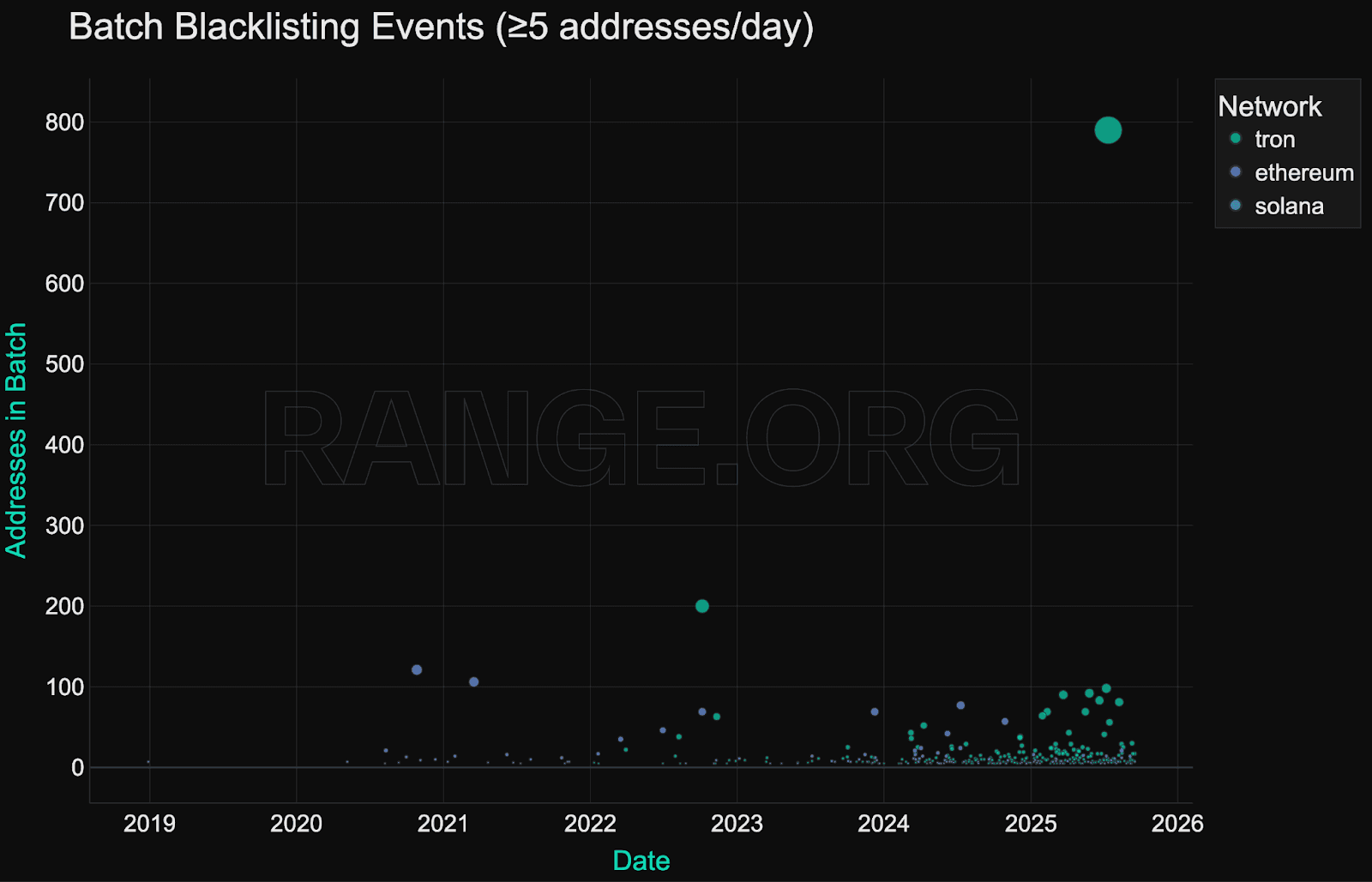
Tron
Tron exhibits the most aggressive batch enforcement behavior. In mid-2025, Tether blacklisted over 800 addresses in a single day - the largest batch event observed across any chain.
As seen in the chart below, these clusters are frequent and sizeable. Tether holds 94% of the enforcement share on Tron, where blacklisting appears focused on mass actions, likely tied to spam, phishing, or automation patterns rather than high-value interventions.
At least two of our observed spikes in Tron activity are related to the work of zeroShadow, who sent batch requests for blacklisting in relation to the Ronin Bridge and Bybit hacks. According to the team, Tron is a hotbed of activity, partly because it is a key route for DPRK hackers to cash out their illicit gains (see section on "Sanctions Freezing").
Solana
Solana has the fewest blacklisted addresses but the highest average frozen balance per address at $1.16 million. Enforcement here is rare but selective. Only eight addresses were blacklisted, all by Circle.
Importantly, Solana is the only network with confirmed unblacklisting activity: four reversals conducted by Circle between 2024 and 2025. No other chain has recorded a confirmed rollback of a blacklisted address.
Unblacklisting does happen
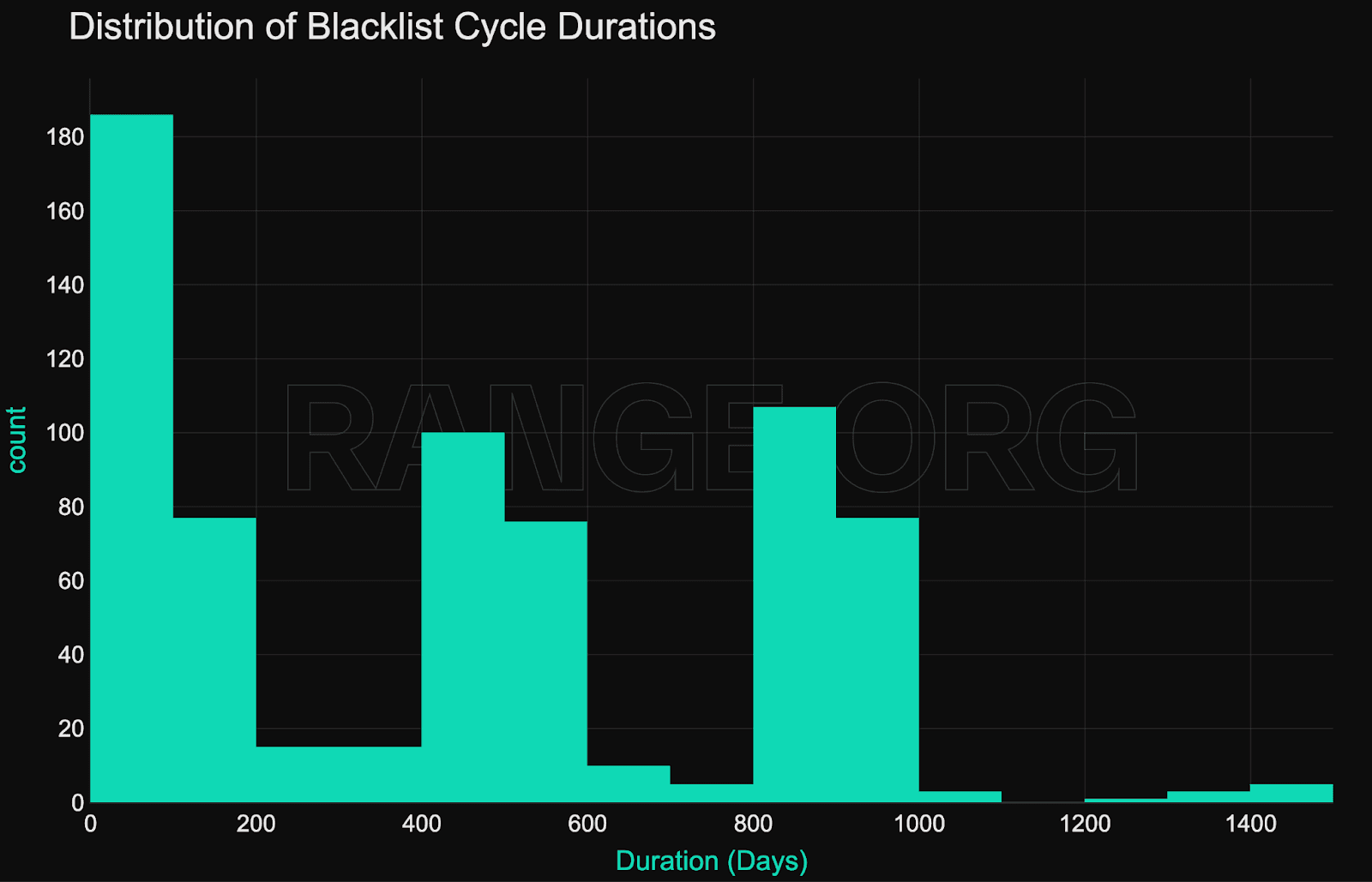
To date, there have been 760 unblacklist events - 381 on Tron, 375 on Etheruem and 4 on Solana. A significant proportion of this took place in 2025 - coinciding with the uptick in enforcement during the year.
Durations ranged from 0 to 1400 days before reversal.
No public reasoning was disclosed.
At least one case involved a Circle Treasury address, raising questions around internal processes or operational errors.
Some of the reversals could be a result of law enforcement-related freezes, which were then unfrozen either when a case was abandoned or when law enforcement bodies were ready to seize the funds. We could not discern any standardized appeals process or consistent timeline.
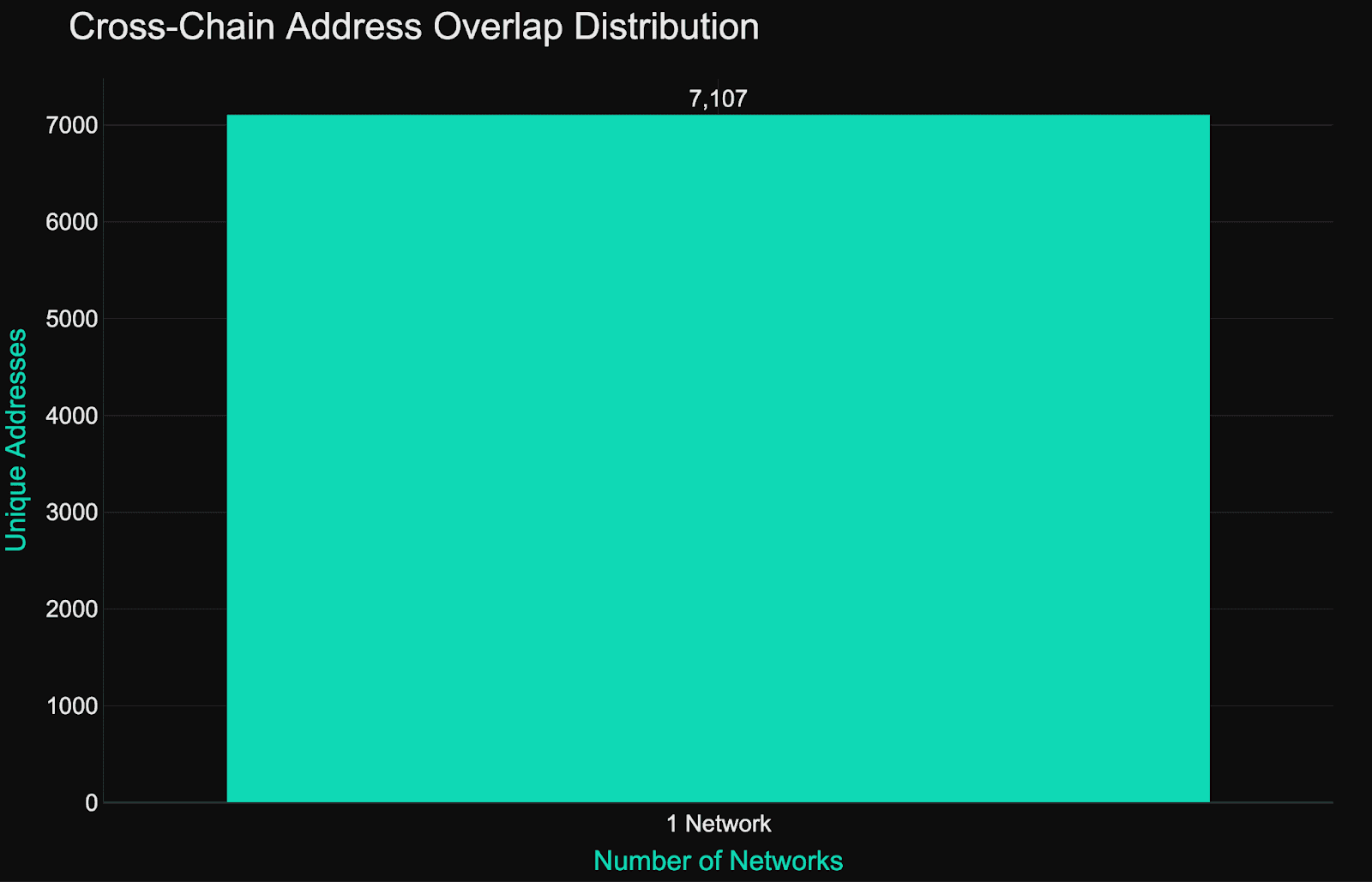
Cross-Chain enforcement (or lack thereof)
Despite 7,107 addresses with frozen assets, cross-chain overlap is virtually nonexistent. Nearly every blacklisted address appears on only one chain, reflecting siloed enforcement pipelines.
This creates obvious risk gaps. If a wallet is blacklisted on Ethereum but remains active on Solana or Tron, the actor can easily route funds cross-chain to evade controls.
Both our Risk API and Faraday suite provide cross-ecosystem tracking of malicious activity - monitoring the same wallet across multiple networks, and identifying cross-chain fund flows to new addresses. This gives our customers a level of visibility and protection that issuer-level blacklisting alone can’t match.
Sanctions Freezing: Follow the assets, not the list
A significant share of Tether’s freezes are linked to illicit flows involving OFAC-sanctioned actors. Working with law enforcement, Tether, Tron, and TRM, zeroShadow identifies freezing opportunities that meet a high evidentiary threshold. These operations require coordination across multiple stakeholders and must account for the fact that sanctioned entities rarely hold funds in static wallets for long. In some cases, teams that failed to detect downstream exposure have seen their own assets frozen as a result.
The core issue is the limitations of list-based compliance. Sanctioned groups actively rotate wallets, move funds cross-chain, and fragment flows through intermediaries that evade first-order screening. Once assets leave a designated address, the original risk is rarely detected by conventional monitoring tools - even as it travels through major platforms.
This is where exposure occurs. Screening against OFAC lists may satisfy a regulatory checkbox, but it doesn’t prevent sanctioned funds from entering downstream systems. For example, one OFAC-designated address tied to the 2025 Bybit hack attributed to DPRK’s TraderTraitor moved nearly $30 million USD in stolen Ether before converting it to Bitcoin. More than 350 newly created addresses were used to obfuscate and fragment the assets to bypass screening checks at a variety of services (you can read more about zeorShadow’s work to support Bybit here).
The visualisation below shows the laundering sequence for the cleaning of that $30m USD, with each node representing an address cluster and each edge a transfer.
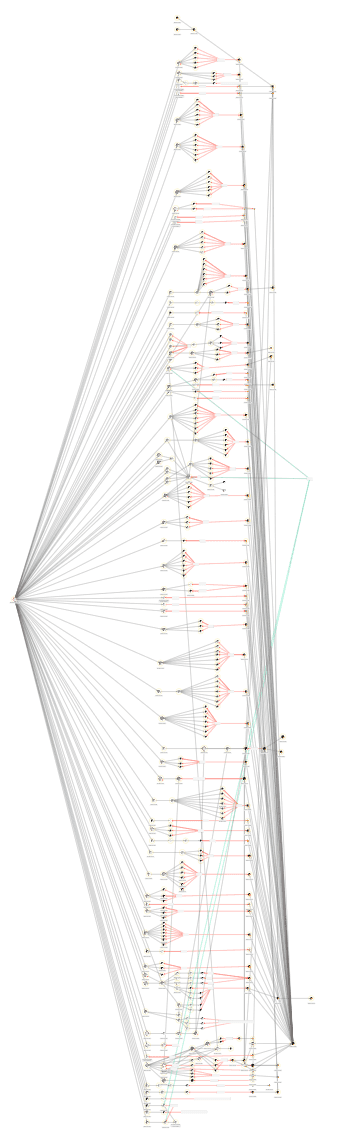
That example involves just one OFAC-designated address. zeroShadow currently tracks 29,559 DPRK-linked addresses, and their laundering routes are engineered to exit through stablecoins at OTC desks. Direct exposure to these downstream pathways presents clear sanctions and freeze risk, and compliance teams need visibility into this movement rather than relying on a list published months or years earlier.
To address this, zeroShadow has partnered with Range to provide live intelligence on active DPRK and other sanctioned laundering flows. This enables real-time screening of cross-chain activity, closing the gaps left by list-based tools and helping teams prevent tainted assets from entering their platforms.
Compliance is a minefield
Blacklisting has become an essential part of stablecoin infrastructure. But enforcement today is:
Asymmetrical – with a few high-value targets driving the majority of frozen value.
Single-chain – with negligible cross-chain coordination or duplication.
Issuer-led – dominated by internal enforcement logic, not regulatory compliance.
A key issue our research has found is the effectiveness of OFAC monitoring. Most compliance providers use static lists provided by OFAC, but in practice, it fails to capture the downstream movement of funds. Once assets leave a sanctioned address - often via a simple bridge or DEX transaction - their origin becomes increasingly difficult to track using static list-matching. Most compliance systems rely on these basic first-order address checks, which are easily circumvented in a cross-chain environment.
Range and zeroShadow addresses this risk with real-time, cross-chain tracing of wallet behavior. Combined with data from zeroShadow, our Risk API and Faraday suite surface downstream exposure even when assets are bridged or passed through intermediaries, enabling teams to monitor for sanction-related activity beyond static lists- allowing you to maintain a higher standard of enforcement across chains.
With over $1 billion in frozen assets and stablecoins now embedded in both DeFi and institutional workflows, onchain enforcement needs to evolve - from reactive, single-chain policies to coordinated, cross-chain risk systems that reflect how users actually move across ecosystems.
Faraday was designed for this shift. It provides a unified enforcement and monitoring layer for stablecoins that aggregates issuer actions, sanctions lists, and cross-chain wallet behavior into a single, reliable system. Together with our Risk API, Faraday gives teams the intelligence they need to identify high‑risk actors, block cross‑chain evasion patterns, and enforce consistently across every network they support.
Book a demo to see how Faraday can help your stablecoin product operate safely.
Be the first to read the next research piece by joining our mailing list >>
About Range
Range is the leading intelligence and risk platform for cross-chain stablecoin infrastructure, trusted by the Solana Foundation, Circle, Stellar, dYdX, Squads and more. We provide the compliance, risk, and routing systems behind the next generation of onchain payments and applications.
Used by fintechs, protocols, and DeFi teams, Faraday is our transaction engine that enables cross-chain routing, compliance enforcement, and real-time risk monitoring through a single API. Our Stablecoin Explorer at explorer.money - the first of its kind - tracks almost 200 stablecoins across all chains and bridges.
We also provide the security layer behind some of the most sensitive infrastructure on Solana. Our Solana Transaction Security Standard, protects programs, accounts and treasuries worth over $30b, while our Risk API and Onchain Risk Verifier enable privacy-focused apps on Solana to stay compliant.
Whether you're building programmable treasuries or privacy flows, Range helps ensure they're safe, compliant, and ready for scale.