Security
Tracking the Mars Protocol exploit: A $973K attack in 5 hops
On December 14, 2025, Mars Protocol was exploited for just under $1 million. In this article, we use Range Trail to trace both the source of the attacker's funding and the cross-chain path the stolen funds took.

Max G., Syed C.
·
Dec 19, 2025
On December 14th, 2025, Mars Protocol – one of the Cosmos ecosystem’s flagship DeFi projects – suffered a critical exploit on its Perpetuals (Perps) product on Neutron. In less than a few minutes, the attacker drained over $973,000 in USDC from Mars’ lending markets and exited the Neutron chain via a cross-chain route that ultimately led to Binance.
This post traces the attacker’s footprint using Range Trail – our cross-chain forensics platform – and outlines how the stolen funds moved across five addresses and two ecosystems with zero real obfuscation or laundering attempts.
A technical breakdown of how the exploit worked will be published in Part 2. Be the first to read that article by joining our mailing list.
How the exploit worked – A quick primer
Unlike prior attacks on oracle-based perp protocols that manipulated price feeds, the Mars exploit targeted the incentive mechanics and architecture design of the system itself:
Skew-based pricing was used to generate risk-free profit through same-block arbitrage.
Funding rates - meant to penalize imbalanced positions - weren’t applied within the same block, removing downside risk.
Losses from the perp vault were passed to lending depositors, turning passive lenders into exit liquidity.
By looping this pattern 15 times, the attacker extracted over $970K in a matter of seconds. The deeper issue wasn’t a bug in code, but a failure in how mechanisms interacted across the protocol’s components, especially under adversarial conditions.
So where did the money go?
Using Range Trail, our cross-chain flow-of-funds intelligence tool, we traced the attacker’s movement immediately after the exploit concluded. The attacker wasted no time in moving the funds cross-chain.
The exploiter neutron14uk0xh7qf0q65f96x506yjjagya7wrx4hy3kvp used $49,783 USDC to fund two attacking smart contracts on Mars Perps and extracted a total of $973,079 USDC from the lending pools using the exploit we will detail in part 2.
Once the exploit was complete, the attacker moved fast. Using IBC, the funds left Neutron immediately, routing through Noble and into Circle's Cross-Chain Transfer Protocol (CCTP).
The IBC packet payload tells the story. Inspecting the memo reveals the CCTP destination domain 6 (Base) and a base64-encoded recipient address:
Decoding mint_recipient gives us the first Base address: 0xff88979bcbb579008debc5d6c108221804ee44b5.
Plugging this into Range's trail dashboard, the full picture emerges.
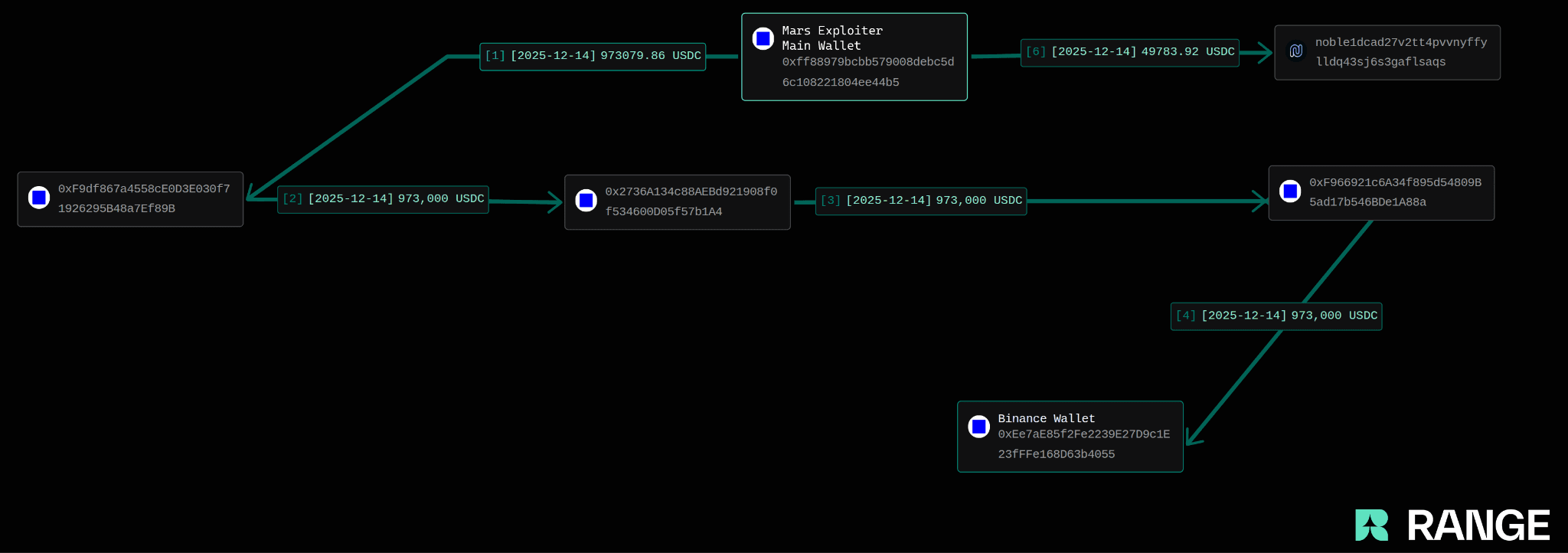
The Money Trail: Neutron to Base to Binance in 5 hops
What followed was a textbook layering pattern. Surprisingly, the attacker did not use any mixer, DEX or privacy tool, opting instead to go straight to centralized exchange cashout.
Each address in the layering chain passed the full amount (~$973K) downstream in a linear sequence, making it fairly simple to trace.
Hop | Address | Amount | Notes |
|---|---|---|---|
-1 |
| - | The two attacking contracts |
0 |
| $973,079.89 | Exploiter origin (Neutron) |
1 |
| $973,079.89 | CCTP landing zone (Base) |
2 |
| $973,000.00 | First Base wallet |
3 |
| $973,000.00 | Intermediate hop |
4 |
| $973,000.00 | Final staging address |
5 |
| $973,000.00 | Binance |
By the fifth hop, the full amount had been deposited into a known Binance hot wallet, likely in preparation for off-ramping or mixing through centralized liquidity.
The speed and simplicity of the attacker’s laundering path is almost brazen. The attacker didn’t use a mixer, privacy coins, or cross-chain DEXes. They moved nearly $1M using only:
IBC (Neutron → Noble)
CCTP (Noble → Base)
5 linear wallet hops on Base
This is significant because it highlights:
The speed and reliability of CCTP as a laundering vector
The lack of cross-chain monitoring on Cosmos-originating funds
How centralized exchange deposit addresses remain common endpoints for exploit flows
In this case, Binance now holds funds traceable directly to this confirmed exploit - and identifying these flows is a critical first step for incident responders, exchange teams, and the Neutron ecosystem.
NOTE: we do not include the IBC forwarding address noble1dcad27v2tt4pvvnyffylldq43sj6s3gaflsaqas a hop above.
So where did the funds come from?
Above, we traced the stolen funds' ultimately destination. In a surprising move, the proceeds of the exploit were moved cleanly and transparently into a Binance customer deposit wallet.
But before the exploit could happen, the attacker first had to fund their operation. Once again, we turned to Range Trail to work backwards.
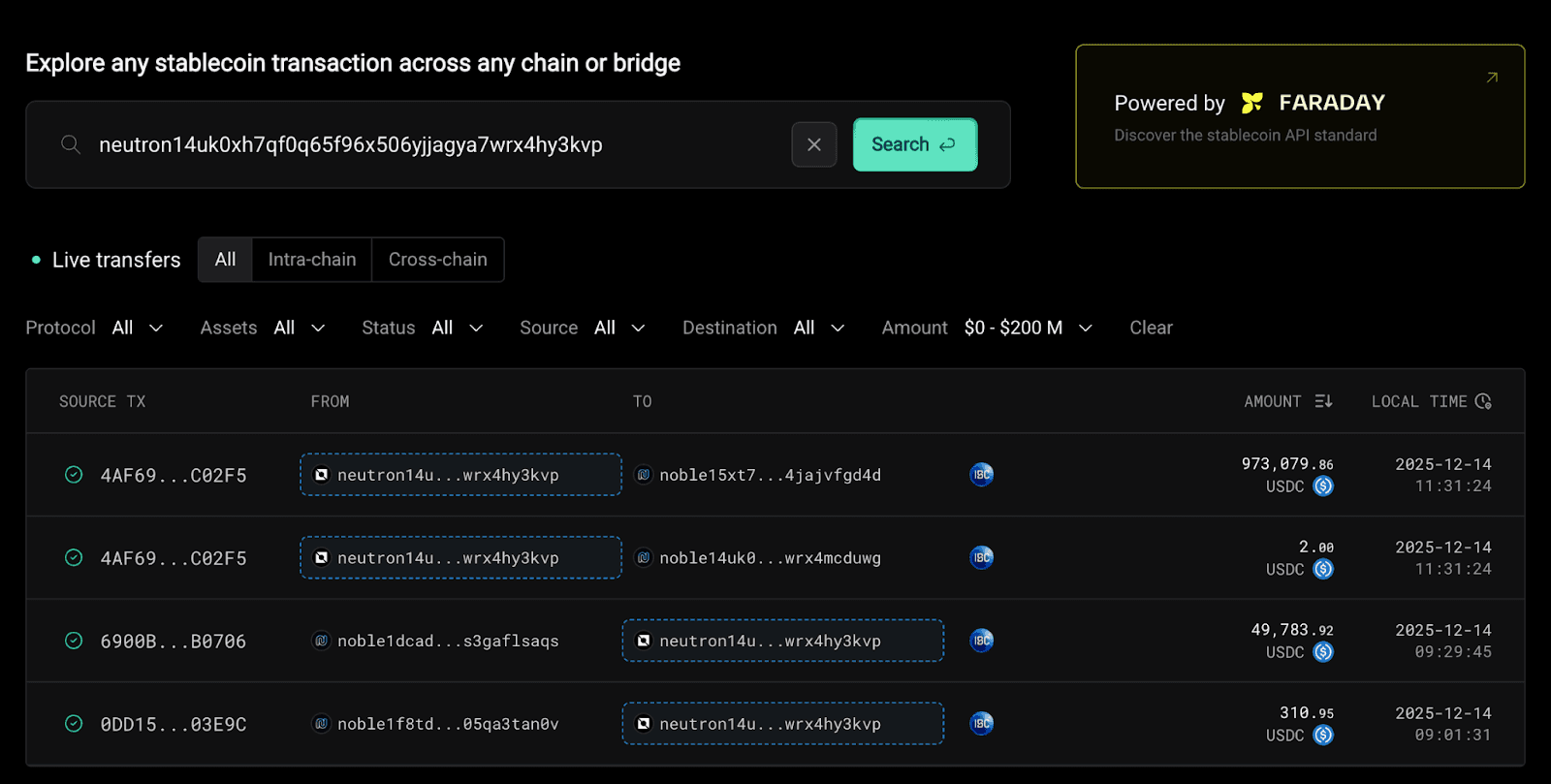
Looking again at the expoiter’s Neutron address - neutron14uk0xh7qf0q65f96x506yjjagya7wrx4hy3kvp - we see that roughly two hours before the exploit concluded, the address received two inbound IBC transfers: 310.95 USDC, followed shortly by 49,783.92 USDC. These deposits provided the capital used to deploy and operate the attack contracts. The next question was obvious: who sent them?
Tracing the smaller transfer first, we can see that the initial ~310 USDC arrived on Neutron (3kvp) via an IBC transfer from Noble - the USDC chain of the Cosmos ecosystem.
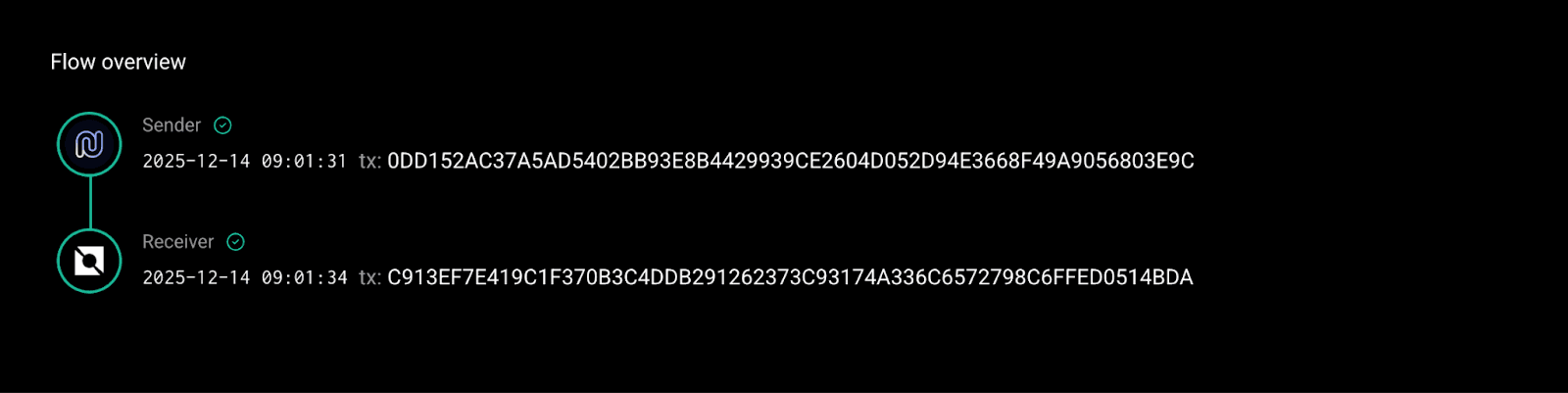
Working backwards through the IBC path shows the funds moving from Osmosis, through Noble, and into Neutron using Skip Go’s routing contracts. Decoding the transaction payload reveals the original sender on Ethereum: 0xFF88979BcbB579008DEBC5D6C108221804EE44b5. This is the same address that later receives the proceeds of the exploit.
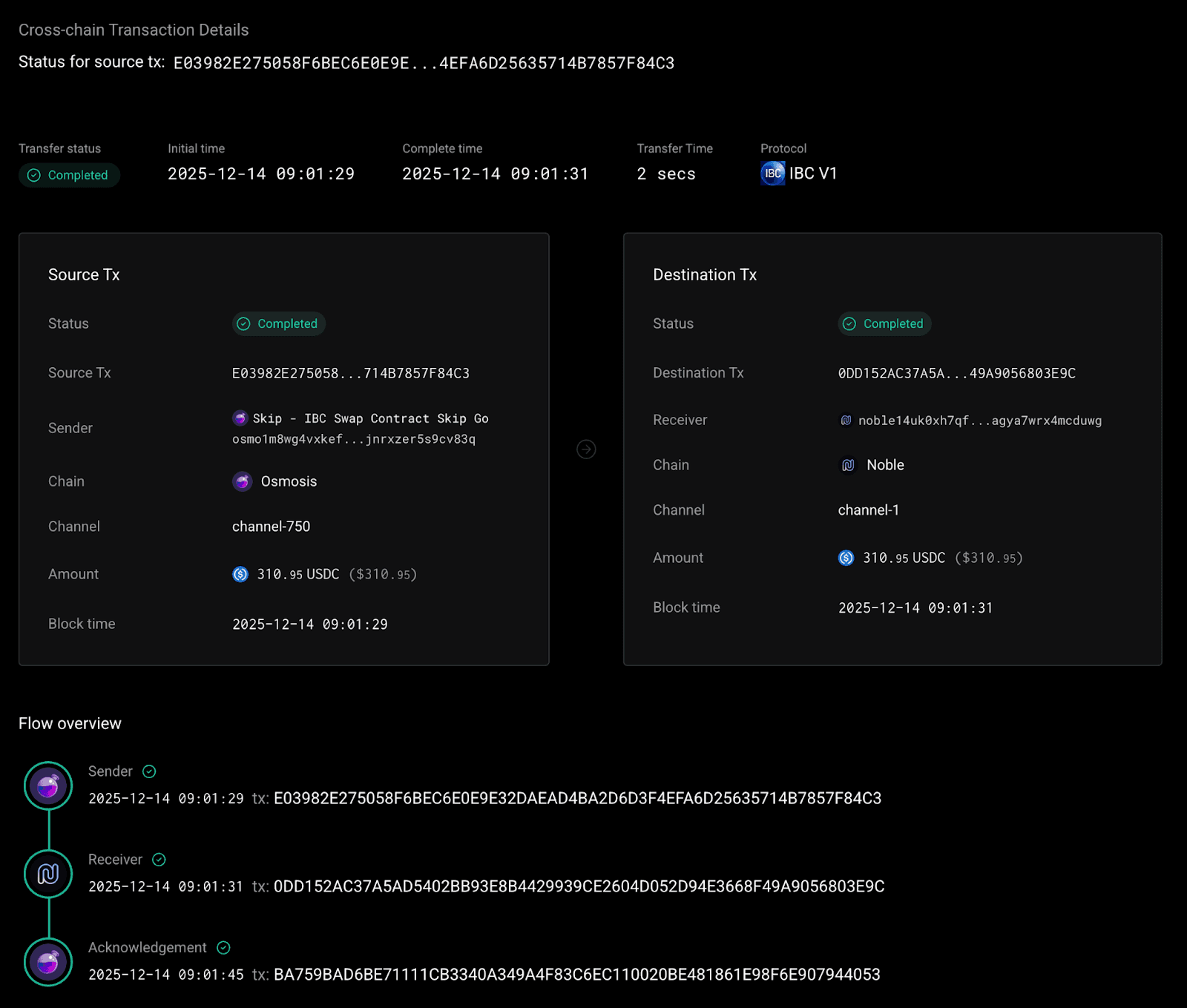
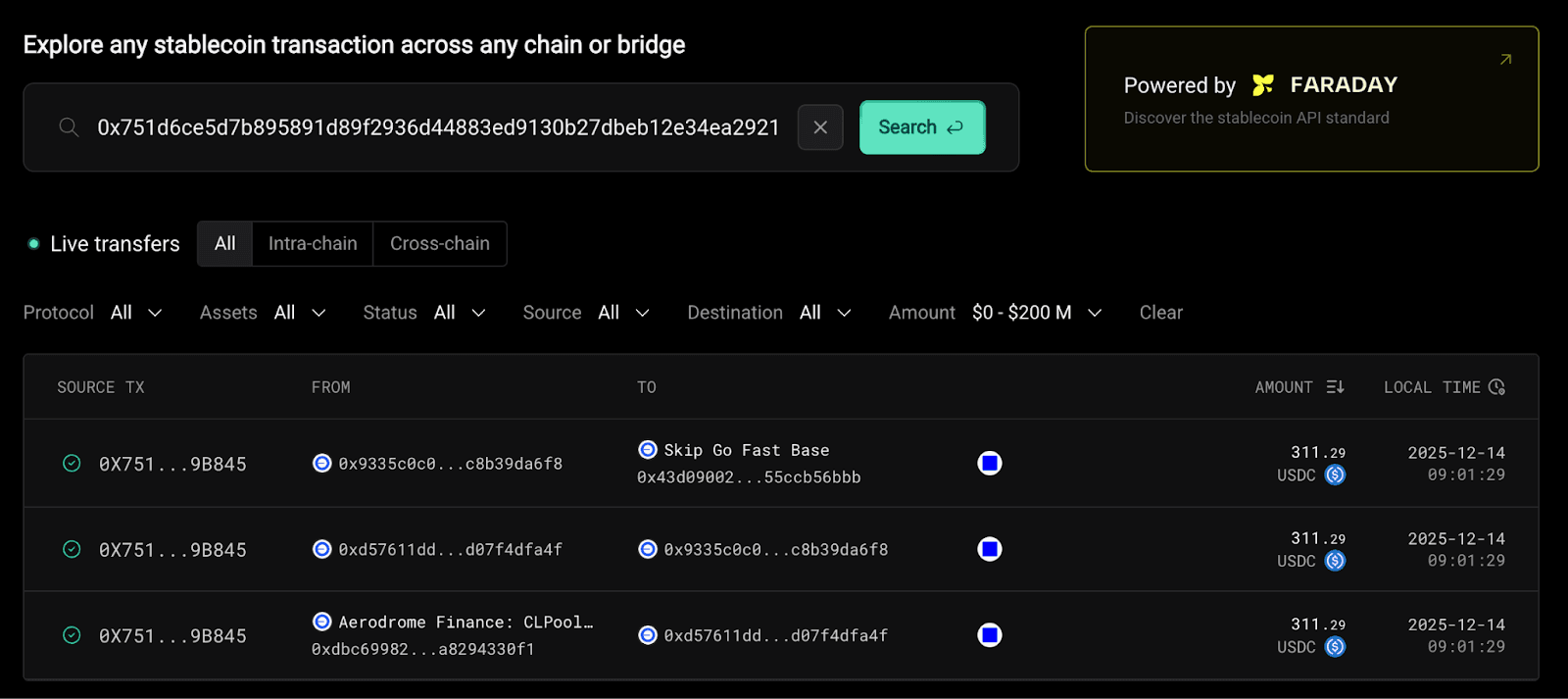
Reviewing activity on this Base address (44b5) fills in the next part of the picture. The address used the Aerodrome DEX to swap wETH into USDC, which was then bridged through Skip and IBC to fund the exploiter’s Neutron account. That brings us to the final piece of the puzzle: how was this Base address funded in the first place?
Looking at the earliest transactions for 0xFF88979BcbB579008DEBC5D6C108221804EE44b5 - on Base and Ethereum, we see that it was initially funded via multiple withdrawals from Tornado Cash, the infamous mixer.
Given the post-exploit flow of funds, this funding source raises an interesting question: if the attacker was sophisticated enough to use a mixer when funding their operation, why were the stolen funds later moved directly into a centralized exchange without similar obfuscation?
While the use of a mixer makes attribution trickier, it does not make it impossible. Advanced analysis - including timing correlations, value fingerprinting, and cross-transaction heuristics - can often narrow down likely deposit sources or link activity across incidents. This is exactly the type of analysis Range performs for protocols, exchanges, and ecosystem teams, turning what looks like a dead end into actionable intelligence.
Below is a list of transactions associated with the attacker’s 44b5 wallet on Ethereum L1 and Base - all occurring in the minutes leading up to the Mars Protocol exploit. For clarity, we’ve excluded the ten Tornado Cash deposits that originally funded the wallet, totaling 16.22 ETH. Notably, seven of those deposits were received nearly a month before the attack, indicating that the wallet was funded and staged well in advance.
From | To | Token | Value | Transaction Hash |
|---|---|---|---|---|
0xFF88979BcbB579008DEBC5D6C108221804EE44b5 | 0xF9df867a4558cE0D3E030f71926295B48a7Ef89B | USDC | 973000 | 0xae609e95cf98911c8cd846fd3a202fb9457990a23f2d6644c331923db4694b4c |
Null Address (0x000) [CCTP / Mint] | 0xFF88979BcbB579008DEBC5D6C108221804EE44b5 | USDC | 973079.862751 | 0x38344dccd3fb49835ee067d9bf60b91134dc604d51a448c1c6c18e81350e52c0 |
0xFF88979BcbB579008DEBC5D6C108221804EE44b5 | CCTPRelayer (Proxy) | ETH | 15.999992287966 | 0x6899c98c2b3809f83f8c208b4f94c97aae4825a07026c14a626914cd35ec2d55 |
0xFF88979BcbB579008DEBC5D6C108221804EE44b5 | GoFastHandler (Proxy) | ETH | 0.01 | 0x70814fc5b16f1c3f1d9665e622f20d8b3a3393f92524335f1c4992eae54635c6 |
0xFF88979BcbB579008DEBC5D6C108221804EE44b5 | GoFastHandler (Proxy) | ETH | 0.0999922888276961 | 0x751d6ce5d7b895891d89f2936d44883ed9130b27dbeb12e34ea2921d63c9b845 |
WrappedEther (0x66a) | 0xFF88979BcbB579008DEBC5D6C108221804EE44b5 | ETH | 16.21 | 0xb063038cc17cb0d4469578ccdb954bcf57c22b51c07ec43f893a4bc0eaa54456 |
Stablecoin infrastructure is being used to exit hacked funds
The Mars incident is a case study in why real-time cross-chain visibility is no longer optional - Funds from exploits are increasingly routing cross-chain.
Without tools like Range Trail, detecting and investigating these flows is nearly impossible at operational speed.
If your protocol, chain, or ecosystem needs to trace fund flows in real time - or set up automatic alerts for risky addresses - our API and platform are available to support both monitoring and incident response.
The Mars exploit shows how stablecoin infrastructure - designed for speed and interoperability - can just as easily be used to exit hacked funds. Nearly $1M in USDC was extracted and moved off Neutron within minutes, routed through IBC and Noble, bridged via Circle’s CCTP, and deposited into a Binance hot wallet in just five hops. No mixers, no swaps - just stablecoin rails operating as intended. For security teams, this kind of flow is almost invisible without active, cross-chain observability.
Range provides the tools to detect and respond to these movements in real time.
Our Risk API lets apps and bridges screen counterparties before execution, with wallet-level scores and behavioral tags tailored for stablecoin risk. Range Trail enables deep forensic tracing across chains, making it easy to follow the flow of exploited funds like this one. With our Real-Time Monitoring & Alerts, teams receive alerts when high-risk wallets move stablecoins, hit thresholds, or interact with your protocol.
And with Faraday - our all-in-one API for stablecoin operations - you can easily orchestrate cross-chain, multi-asset stablecoin deposits and withdrawals from your app, all actively screened for both counterparty and transaction risks, fully compliant with multi-jurisdictional regulations.
As stablecoin rails become the preferred cash-out path for attackers, proactive monitoring is no longer optional. Range gives your team the tools to see, respond, and stop the flow - across chains, in real time. Book a call to explore how we can help you.
Next: How the Mars exploit worked
In Part 2 of this series, we’ll walk through the exploit in technical detail, including:
The attack contract logic
The skew manipulation loop
Why Mars’s architecture amplified losses
And what protocols can learn from the incident
Be the first to read that article by joining our mailing list.
About Range
Range is the leading intelligence and risk platform for cross-chain stablecoin infrastructure, trusted by the Solana Foundation, Circle, Stellar, dYdX, Squads and more. We provide the compliance, risk, and routing systems behind the next generation of onchain payments and applications.
Used by fintechs, protocols, and DeFi teams, Faraday is our transaction engine that enables cross-chain routing, compliance enforcement, and real-time risk monitoring through a single API. Our Stablecoin Explorer at explorer.money - the first of its kind - tracks almost 200 stablecoins across all chains and bridges.
We also provide the security layer behind some of the most sensitive infrastructure on Solana. Our Solana Transaction Security Standard, protects programs, accounts and treasuries worth over $30b, while our Risk API and Onchain Risk Verifier enable privacy-focused apps on Solana to stay compliant.
Whether you're building programmable treasuries or privacy flows, Range helps ensure they're safe, compliant, and ready for scale.




